Welcome to Episode 4 of my Learn stuff series. You’ll remember that in Episode 3 we managed to crack the hash that we captured using responder in Episode 2. This now means that we have a username and password combination.
This is great! But, in an engagement what are the next steps? What can we do with this and ideally what are we looking for?
As always with this series, there is a video which goes through the same steps, this is available here: https://youtu.be/5XkwDsCrBig
Table of Contents
What do we have?
Well in the last episode we managed to crack the hash using both JohnTheRipper and Hashcat using a bespoke wordlist we created with Cewl.
This means that we now have credentials for a user on the domain:
Username: Tardis\Rose Password: Mickey1
Where next?
So, what can we do with that? This is where the tool smbclient comes into play. This tool is built into Kali and let’s us use our Kali instance to try and connect to SMB shares. This are often known to end users as “Z drive” or similar.
They are a central repository for files that are hosted on a physical machine on the network. Often most users will have access to the share’s although some may be restricted based on security groups within Active Directory, keeping really sensitive data private e.g CEO e-mail backup!
Impact
Often within CTFs when looking at SMB it’s when hunting for a password, or a database that contains a password, but in the real world this might not be the most juicy of targets. Sure a password might get you into another system, but it’s likely all the information you need is within these shared files.
So what should you be looking for?
- Clients lists
- HR documentation (Hiring/Firing/Disciplinary action)
- Salary details
- Business plans – buy outs, major inventions etc
- Financial records
All of these could have a bigger impact for a company than just a password for another system. Think of the damage an attacker could do if they got a list of everyone the company had fired, or the stock market implications if a buy-out was about to happen.
If an attacker got a full client list with details, they could then use this information to perform phishing attacks on other companies with an almost guaranteed in!
All of these are highly sensitive data that could have huge ramifications for a company. If you are doing a real-world engagement, these are the things that need to be fed back.
What else?
Well, if you have write permissions, which is likely, you could put a file onto the share. Something named “2019-2020 salary details.xlsm” would be enticing for anyone to click on. The embedded macro (who noticed it was .xlsm?) could then pop a reverse shell, or make a request to our SMB share to capture more credentials or a range of other attacks that would further our foothold in the network.
So how does it work?
Well first up, we have TheDoctor with some shared drives on it.
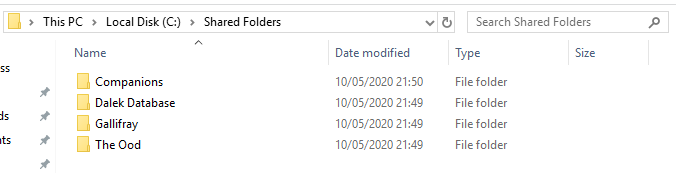
These files are accessible to users within the domain that have the correct level of access!
So from Torchwood it’s now possible to use SMBClient to gain access to those files. SMBClient can check for anonymous access, which is widely used within CTFs:
smbclient -L \\10.10.20.88 -U anonymous
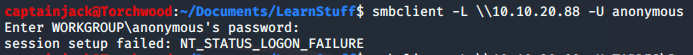
However in this instance, the shares require authentication against the server. This is the default settings within Server 2016 & 2019 , so finding anonymous shares is going to be become a rarity outside of CTFs.
For SMBClient there always needs to be double the amount of backslashes, this is due to the backslash being the escape character in python, so you have to escape the escape for it to work! If your command doesn’t work, check the number of backslashes.
Next up, we can use the credentials that we have. The W flag is for the workgroup, in this case the TARDIS domain and the U flag is for the username.
smbclient -L \\10.10.20.88 -W TARDIS -U Rose
We can see that there are a few different shares available to us, but note that not all shares are available:
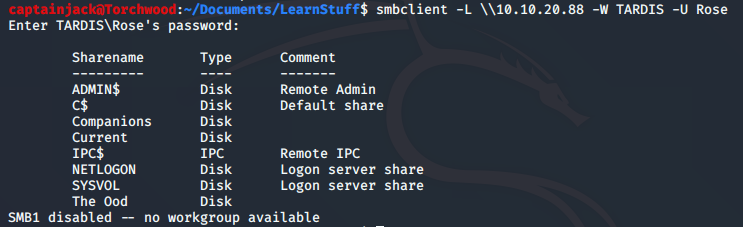
For example the user Rose doesn’t have access to the “Dalek Database” or “Gallifray”. This means that it might be required to compromise another user to gain further access!
However, we do have some shares that are available and we can access them using:
smbclient \\\\10.10.20.88\\Companions -W TARDIS -U Rose
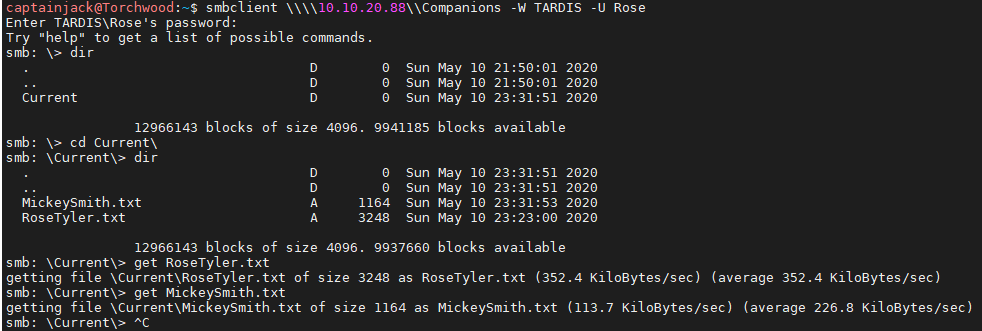
It’s also possible to download all the files onto the local machine using the get command, allowing for offline searching at later time.
Looking at the wireshark traffic for this, it looks very similar to a legitimate SMB request, so it would be difficult for a sysadmin to find within the logs.
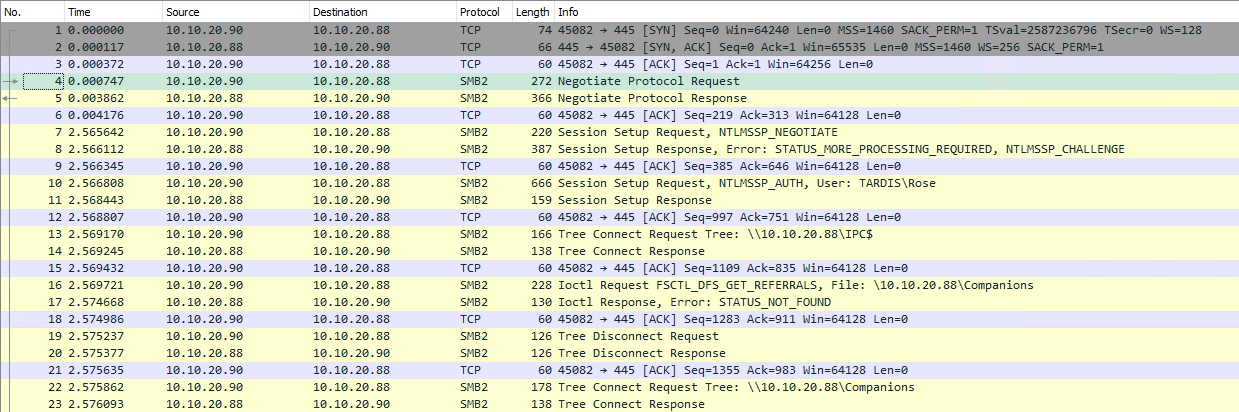
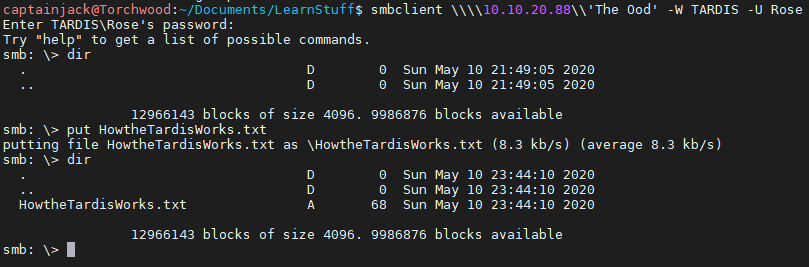
It’s also possible that the user has write access to the share. This can allow malicious files to be uploaded, or if there is LFI within a web application your own code can be run, which again is a CTF favourite.
We can upload files using the put command:
put HowtheTardisWorks.txt
That’s all folks!
This is a really effective tool, with the traffic looking like real requests in an area that there is generally a lot of traffic doing similar. This allows hunting for those sensitive files with potential for company secrets, additional phishing material or passwords for more systems!
The only problem is you may not know where the shared files are stored and that’s where a tool called CrackMapExec (CME) comes in to play! On the next Episode I’ll take a look at using CME to hunt for SMB shares and using the credentials for further access!
Hey!
Sorry I’ve not got twitter and couldn’t find an email to contact you on.
I saw the tweets about the 5g usb stick and look – a quick search of “128mb usb stick” on AliExpress brings up this – £2.27 68% Off | Custom Logo Crystal + Silver Metal USB Flash Drive 2.0 TOYOTA Pendrive 4GB 8GB 16GB 32GB 64GB Memory Stick 128MB U Disk for Gift
https://a.aliexpress.com/_dUkBk9h
If you order more than 10 you get your logo personalised for free!!
I cannot even get MY OWN samba to work lol